As enterprise digitalization and IT maturity continue to advance, more business systems have moved online, become platform-based, and are managed centrally. Yet in many real-world workflows, USB drives, portable hard disks, and other physical storage media remain irreplaceable. This is especially common in manufacturing, R&D, engineering, energy, and rail transportation, where the following scenarios occur frequently:
-
Production control networks, test networks, and office networks are logically isolated, so data can only be imported/exported via USB drives.
-
R&D design files, process drawings, and source code must be delivered and transferred across multiple systems and teams.
-
Document and data handoffs with contractors, suppliers, and partners still rely heavily on physical media.
-
On-site environments may not have network connectivity, so data must be circulated, backed up, and delivered offline.
USB convenience boosts efficiency, but its “plug-and-play” nature also means it inherently lacks strong control. Without technical governance measures, USB devices can quickly become a primary channel for data leakage, non-compliant external transfer, malware propagation, and unclear accountability. Many security incidents have shown:
The real cause of leaks is often not hacker attacks, but internal non-compliant copying—whether accidental or intentional.
Therefore, the core question for enterprises is not “Should we use USB drives?”, but:
How can we govern USB usage effectively without disrupting business, so data remains “usable, controllable, and traceable”?
Ping32 was built around this practical need, delivering an enterprise-grade system for fine-grained USB governance and secure offline data circulation—so physical media is no longer a blind spot in your security program.
Invisible, Uncontrolled, Untraceable: The Real Challenges of USB Sprawl
In many organizations, USB usage has long been “allowed by default.” As long as the operating system recognizes a device as storage, it can be freely connected to endpoints—whether it’s a personally purchased drive, a promotional freebie, or an unknown external device. This leaves enterprises with little to no security threshold at the device layer, allowing malicious or infected devices to enter internal networks and become a hidden source of risk.
Even when USB usage is permitted, organizations often lack visibility into what actually happens. Did an employee copy more than what their job required? Did they take core technical documents, customer information, pricing strategies, or business data outside the company environment? Was there an “extra copy just in case” behavior? These actions often go unnoticed until a leak erupts—at which point losses may already be irreversible.
During post-incident investigations, enterprises frequently face a “can’t prove it” dilemma:
-
Without complete logs, it’s impossible to reconstruct who copied which files, when, from which endpoint, using which device.
-
Without accountability mapping, responsibility cannot be clearly assigned and governance cannot be enforced.
-
Internal investigations can devolve into speculation and blame, solving nothing while damaging organizational trust.
Under these conditions, management often swings between two extremes: a blanket USB ban that blocks business workflows—pushing employees to bypass controls using personal devices or cloud drives, creating even bigger blind spots—or total openness that relies on policies and self-discipline, allowing risks to accumulate silently. The trade-off between security and efficiency becomes an unavoidable governance challenge.
Ping32 USB Governance: Building a “Controllable, Auditable, Accountable” Usage System
Across manufacturing, R&D, and engineering scenarios, USB devices and portable storage remain essential tools for data transfer. Yet they have historically sat outside the enterprise security perimeter—hard to see, hard to control, and even harder to hold accountable. Ping32’s portable media governance capability is designed to address this reality by bringing removable storage into a unified framework that is manageable, auditable, and traceable—without sacrificing operational efficiency.
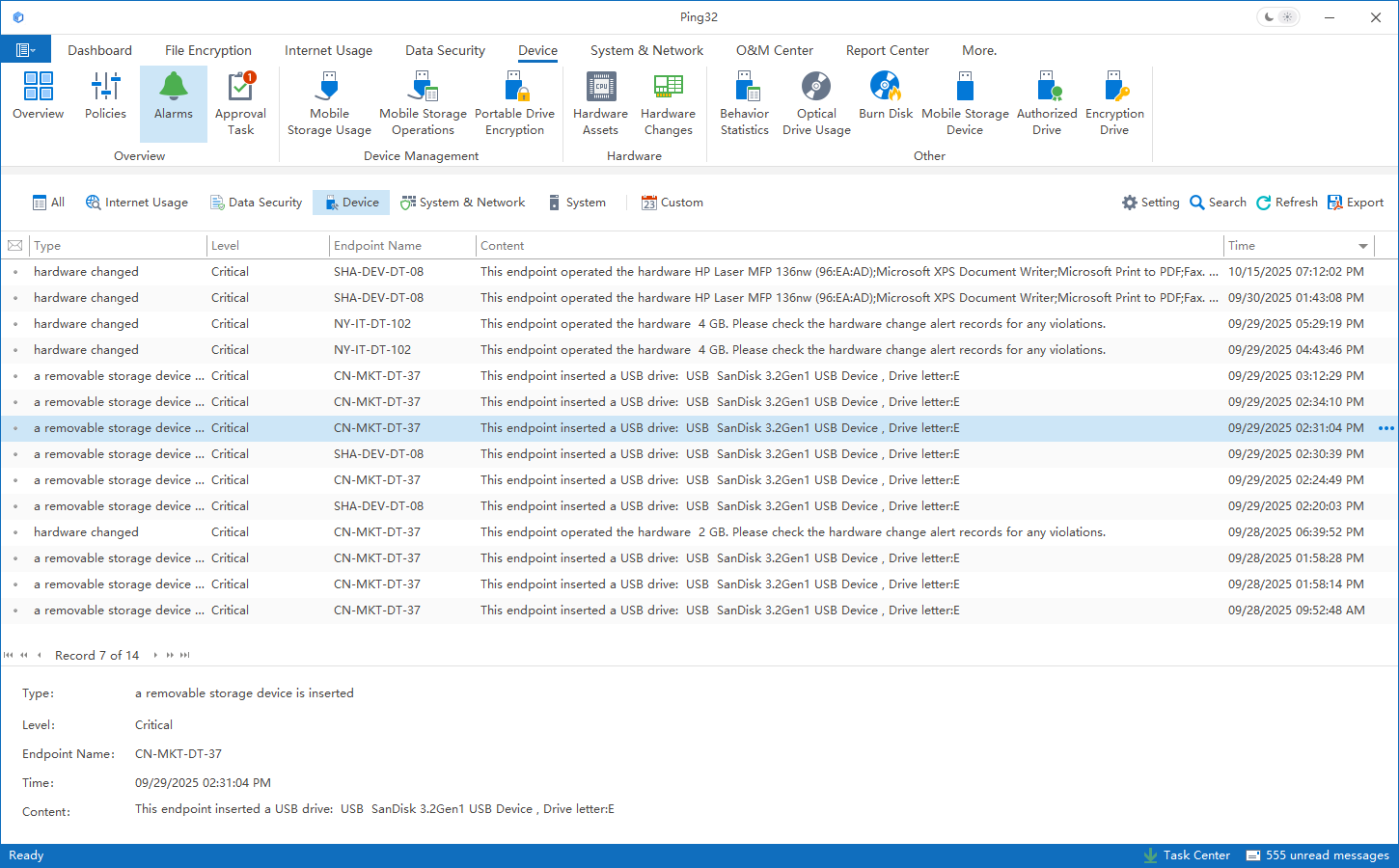
When an employee inserts a USB device into an endpoint, the system automatically identifies the device source and records plug/unplug events. It then captures a complete audit trail of subsequent file operations, including read, write, copy, and delete actions. Security and IT administrators can clearly see:
Who did what, when, on which endpoint, using which USB device, and which files were handled.
This turns previously opaque offline circulation into a transparent, searchable process. If a USB device is used outside business hours, on an unauthorized endpoint, or in abnormal scenarios, the system can trigger real-time alerts—so risks are surfaced during the event, not after damage is done.
Organizations can also standardize USB usage based on business needs, for example:
-
Allow only company-approved USB devices, automatically blocking personal, unknown, or external devices.
-
On R&D endpoints, allow import only and prohibit export.
-
For roles handling sensitive assets, restrict copying of specific files or specific data types.
These controls are not blunt “business blockers.” They keep essential workflows running while precisely constraining high-risk behavior to a manageable range.
When exceptional USB usage is necessary, employees can request temporary read/write access through an approval workflow. Once approved, the authorization is granted, and the full authorization and usage process is logged, forming an auditable closed loop.
For data that is permitted to be carried out but remains sensitive, Ping32 can encrypt the USB device. Encrypted USB media can only be used on authorized endpoints and within authorized user/account contexts inside the organization. Even if an employee takes the USB device outside the company in violation of policy, files cannot be opened normally on external devices—effectively preventing misuse or uncontrolled spread beyond the organizational boundary.
With this end-to-end mechanism, Ping32 transforms USB devices from an unmanaged “gray channel” into a governed data pathway with rules, records, protection, and accountability—meeting offline business requirements while significantly reducing the risk of information leakage and achieving a practical balance between security and efficiency.
Solution Value: Upgrading from “Patching Gaps” to “Building Governance”
1) Shift Risk Left: From Reactive Response to Proactive Prevention
Ping32’s USB governance is not simply “adding another restriction.” It closes a long-missing capability: offline data governance. With device admission controls, behavior policies, and content protection, organizations can block high-risk scenarios before copying occurs and constrain non-compliant actions during execution—substantially reducing the likelihood of data leakage, policy violations, and malware introduction.
2) Balance Security and Productivity: Avoid the Side Effects of “Ban Everything”
Unlike one-size-fits-all blocking, Ping32 supports differentiated policies by role, department, and scenario—allowing necessary data circulation to continue while precisely limiting risky operations. Security becomes part of the workflow rather than an obstacle, reducing the incentive and opportunity for employees to bypass controls through gray channels.
3) Auditable Compliance: Make Governance Evidence-Based
Comprehensive logs and full traceability enable organizations to reconstruct “who, when, using what, did what to which data.” In regulatory inspections, internal audits, or disputes, teams can rely on facts and records rather than uncertainty—avoiding the passive “we can’t prove it” situation.
4) Clear Accountability: Reduce Friction and Build Trust
Technical evidence replaces subjective judgment. Accountability shifts from ambiguous to clear, helping protect enterprise assets and compliant employees alike. This reduces misattribution and internal friction, and improves transparency and trust in governance.
5) Governance Maturity Upgrade: Lay the Foundation for Long-Term Growth
Over the long term, Ping32 helps organizations evolve from point tools to a governance capability—making offline data circulation a true part of the digital system and laying a foundation for more complex data flows and cross-organization collaboration in the future.
Frequently Asked Questions
Q1: Why do enterprises still need USB devices?
In segmented networks (production/test/office), offline or no-connectivity environments, and supply-chain handoffs, offline media remains the most practical and fastest option. A blanket ban often disrupts operations and encourages workarounds.
Q2: What are the main security risks of USB usage?
Key risks include data leakage and non-compliant external transfer, malware introduction into internal networks, lack of visibility leading to unclear accountability, and insufficient evidence during audits or compliance checks.
Q3: How does Ping32 deliver “usable, controllable, and traceable” USB governance?
Through device identification and admission control (approved devices only), behavior policies (read/write/import/export restrictions), full audit trails, and real-time alerts for abnormal usage.
Q4: Can we allow only company USB devices and block personal ones?
Yes. Ping32 can be configured to allow only approved devices and automatically block personal, unknown, or external removable storage.
Q5: What if we need USB access temporarily for urgent business needs?
Employees can submit a temporary read/write request through an approval workflow. Once approved, access is granted, and all approvals and actions are fully logged.
Q6: If a USB device is encrypted, can files be opened outside the company?
Typically no. Encrypted USB media can be restricted to authorized endpoints and user/account contexts, preventing use beyond the organizational boundary.
Q7: Which industries or departments is this solution best suited for?
It’s especially suitable for manufacturing, R&D, engineering, energy, and rail transportation, as well as teams in design, process engineering, testing, production, operations/maintenance, procurement, and supply-chain collaboration.






 Contact
Contact





































 10 min
10 min 





