As enterprise digital transformation continues to accelerate, the widespread adoption of information systems, cloud office platforms, and online collaboration tools has made electronic document management increasingly standardized. However, printing remains ubiquitous across many business scenarios—contract signing, R&D plans, financial statements, technical documents, and external communications. Compared with digital files, paper output is far more likely to fall outside of control. Once printed documents are taken out of the office, the original access permissions and security policies no longer apply.
In small and mid-sized businesses, especially where printers are shared or centrally used by multiple departments, the lack of transparency in printing activities can introduce potential data leakage risks. At the same time, when an information leakage incident occurs, organizations often struggle to determine whether paper output was involved, making accountability tracking, compliance audits, and risk assessment more difficult.
Therefore, incorporating printing into an endpoint Data Loss Prevention (DLP) framework has become a critical step for building enforceable, secure, and manageable day-to-day operations. Organizations should no longer focus only on electronic data movement—they also need systematic, deployable controls over endpoint printing behavior to reduce potential risks while meeting compliance and audit requirements.
As printing devices evolve from simple local printers to network printing, shared printing, and remote printing, enterprise print management needs have become more diverse. On one hand, businesses must ensure smooth operations and efficient document output; on the other, they must prevent sensitive data from leaking through printing. How to maintain business continuity while bringing printing activities into a monitorable and auditable management scope has become a key topic in everyday information security governance.
Print Risk Sources: A High-Risk Channel That’s Often Underestimated
Within an enterprise DLP program, printing is often viewed as a low-tech, low-risk action. In real-world operations, however, the risk dimensions are far more complex. When employees initiate printing directly from their endpoints, a lack of clear permission boundaries and complete activity logging can result in sensitive documents being printed inadvertently or without authorization.
Once a document is printed, its distribution path quickly escapes the control of digital systems. Paper copies may be taken out of the office, handed to others, or retained for long periods, and the organization can no longer rely on technical means to recall, block, or track them in real time. This makes printing inherently difficult to govern.
In environments where multiple departments share printing devices, accountability can become even more blurred. After the fact, it is often hard to determine who printed a document, when it was printed, and for what business purpose—raising the difficulty of investigations and audits.
In addition, without effective identification mechanisms during printing—such as watermarks or source information—even if a leak occurs, it is difficult to determine the origin from the paper document itself. Many organizations also lack print-approval processes for high-risk documents, allowing sensitive information to be output without prior authorization confirmation and further amplifying security risks in print scenarios.
Real-World Challenges: Why Print Management Often Stays at the “Policy Level”
While most organizations recognize the importance of print security at the policy level, print management is often difficult to implement in practice. Print logs are scattered across different endpoints, printing devices, and even different systems, and the lack of centralized management and analytics makes it hard to form a clear picture of overall printing activity.
At the same time, many organizations struggle to distinguish sensitive documents from ordinary ones at a technical level and therefore rely on broad rules. This approach can both block legitimate business printing (false positives) and fail to cover truly high-risk scenarios (false negatives), weakening overall effectiveness.
For printing behaviors that require stricter control, many organizations lack enforceable approval workflows, leaving policies in place but without real constraint. When stricter restrictions are used to compensate for management gaps, daily productivity can suffer—often triggering internal resistance.
More critically, once paper documents leave the organization, technical traceability is generally limited. It becomes difficult to trace the source or assign responsibility based on the document itself. Print policies and management measures also tend to remain at their initial configuration, lacking continuous adjustment and optimization as business processes and risks evolve. Together, these issues keep print management in a long-term state of “requirements exist, but execution is hard.”
The Ping32 Approach: Combining Monitoring, Control, Approval, and Watermarking
To address the “invisible, hard to control, hard to trace” challenges of print management, Ping32 brings printing activities into a unified endpoint management and DLP system—making printing visible, controllable, and traceable.
First, Ping32 continuously monitors printing behavior on the endpoint. The system automatically records key information for each print job—such as document title, print time, user, endpoint, and printer—and centrally stores it for analytics and compliance audits. It also supports print-content backup, helping organizations determine whether abnormal or inappropriate usage occurred, and establishing foundational visibility into printing activity.
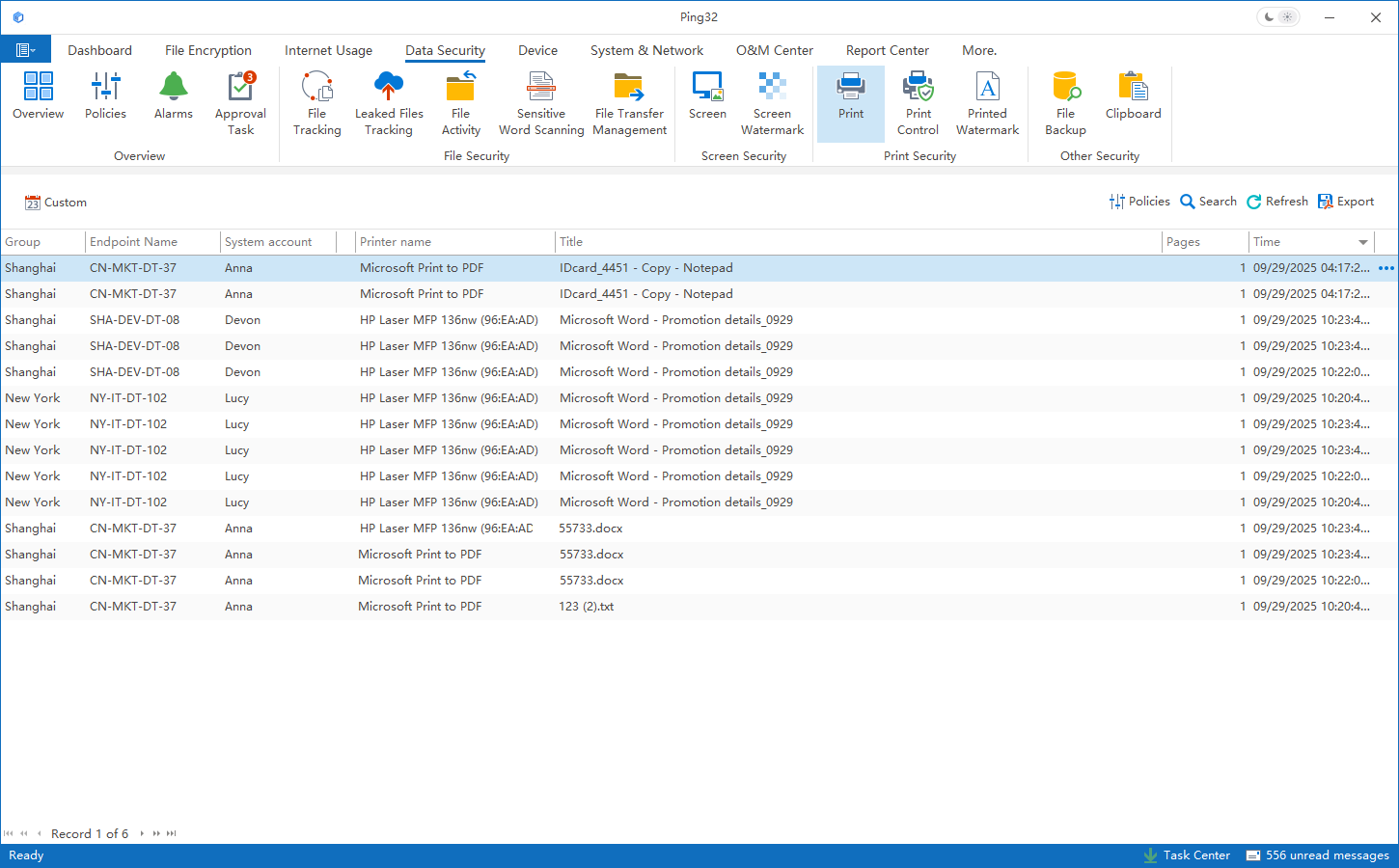
On this basis, the system provides fine-grained control over print permissions. Organizations can configure different print policies by department, role, and endpoint, and restrict print actions that do not meet policy requirements. This risk-based, differentiated approach reduces impact on normal business operations.
For higher-risk but business-necessary print scenarios, Ping32 introduces print approval. Users must obtain authorization before printing, and the approval process records the approver, approval time, and result—forming an auditable workflow trail. This adds essential confirmation and responsibility definition for critical printing behavior without fully blocking business needs.
Meanwhile, Ping32 enhances the traceability of paper documents through print watermarking. The system can automatically add watermarks containing user, department, and time information to printed output to indicate origin, and it also supports disabling watermarks for specific documents to balance security requirements with business needs.
Through the coordination of these mechanisms, Ping32 helps organizations bring printing into a management scope that is visible, controllable, auditable, and continuously optimizable—so printing is no longer a blind spot in data security but an integral part of endpoint data governance.
Implementation Path: Progressive Print Management
To ensure print security management is effectively implemented, the following progressive approach is recommended:
●Enable print monitoring: record printing activity and back up printed files to establish a unified visibility foundation;
●Analyze printing behavior: track print frequency, document types, and anomalous behavior to identify key risk points;
●Enable print approval: apply approval policies to sensitive documents and high-risk users to ensure authorization before printing;
●Add print watermarks: apply traceable watermarks to critical documents to facilitate post-incident accountability checks;
●Continuously optimize policies: regularly review print logs, approval records, and watermark effectiveness; adjust permissions and policies to match business needs;
●Training and governance: train employees on print management and security awareness, clarify approval workflows and responsibility boundaries, and reduce human-error risk.
This progressive approach helps organizations achieve auditable, controllable, and traceable printing without disrupting daily operations.
Conclusion: Bring Printing into an Auditable and Controllable Scope
With the Ping32 print monitoring and control framework, organizations can build a complete visibility and audit chain for endpoint printing behavior. By combining approval workflows and watermarking, sensitive print activity is controlled and labeled—so printing is no longer a data security blind spot but a manageable, traceable, and continuously optimizable part of the overall program.
This framework emphasizes practicality and sustainability while maintaining business continuity. Instead of relying on excessive restrictions to achieve security, it balances print management through a combination of behavior monitoring, permission control, approval traceability, and watermark tracking. In doing so, organizations can reduce paper-based data leakage risks while strengthening internal governance and compliance capabilities.
FAQ (Frequently Asked Questions)
-
Does print monitoring involve collecting employees’ private content?
The system collects only the necessary information related to print behavior. The collection scope is configurable by the organization for audit and compliance purposes. -
Will print approval impact daily printing efficiency?
Approvals typically apply only to sensitive documents and specific users, and usually do not affect routine office workflows. -
Can watermark content be customized?
Yes. It can include user information, print time, department information, QR codes, or text combinations. -
Can we enable print monitoring without restricting printing?
Yes. Monitoring alone can provide visibility and auditability for print behavior. -
Can different departments configure different print permissions and approval workflows?
Yes. Policies can be flexibly configured by department, role, and endpoint.






 Contact
Contact





































 9 min
9 min 





