As digital transformation (DX) accelerates, the security challenges enterprises face are becoming increasingly complex. Traditional defenses are often no longer sufficient to address modern threats—especially data leakage, cyberattacks, and abuse of access privileges by internal or external actors. In this environment, organizations need a more comprehensive and intelligent enterprise data security solution to protect their digital assets and operational security.
Ping32 was built for exactly these needs. As a unified, enterprise-grade security platform, Ping32 brings together endpoint security management, transparent file encryption, DLP (Data Loss Prevention), behavior auditing, and risk assessment in a single system. With intelligent analytics and flexible policy configuration, Ping32 helps organizations build a complete, deployable, and scalable security posture.
1. The Multi-Layer Security Challenges Enterprises Face: From Traditional Controls to Intelligent Security
1) Rising Risks of Data Leakage and Privacy Compliance
Data breach incidents continue to increase globally. When sensitive information is not adequately protected, organizations may suffer financial losses, reputational damage, and legal liability. Under increasingly strict privacy regulations (such as GDPR and CCPA), enterprises must defend not only against external attackers, but also against leakage caused by employee negligence or misuse of data.
In real-world file storage and transfer processes, vulnerabilities commonly arise from misconfigured permissions, fragmented outbound channels, and insufficient security awareness. For high-value information—such as customer data, financial records, R&D documents, and source code—a single leakage event can lead to major penalties and directly impact business continuity and growth.
2) Efficient Data Management and Real-Time Monitoring at Scale
As enterprise data volumes grow rapidly, traditional security tools often struggle to deliver real-time monitoring and intelligent analysis in large-scale, high-complexity information flows. Organizations need an efficient system capable of quickly identifying potential threats within massive datasets—and taking action in time.
At the same time, enterprises must maintain productivity. Fast access, high-speed search, analytics, and report generation create higher demands for system performance and responsiveness—especially under strict security constraints.
3) The Complexity of Internal and External Threats
Security threats come not only from hackers. Improper behavior or mistakes by internal users frequently become the source of data leakage. Many incidents are not caused by technical vulnerabilities, but by operational weaknesses such as loose privilege control, insufficient auditing, and weak governance processes. The challenge is to strengthen privilege governance and outbound control without undermining user experience and efficiency.
2. What Is Ping32: A Platform That Redefines Enterprise Data Security
Ping32 is a comprehensive enterprise data security governance platform designed to address the challenges above. By integrating transparent file encryption, DLP, endpoint security management, behavior auditing, and risk assessment, Ping32 helps organizations enhance data protection, optimize information flow, improve productivity, and maintain compliance during daily operations.
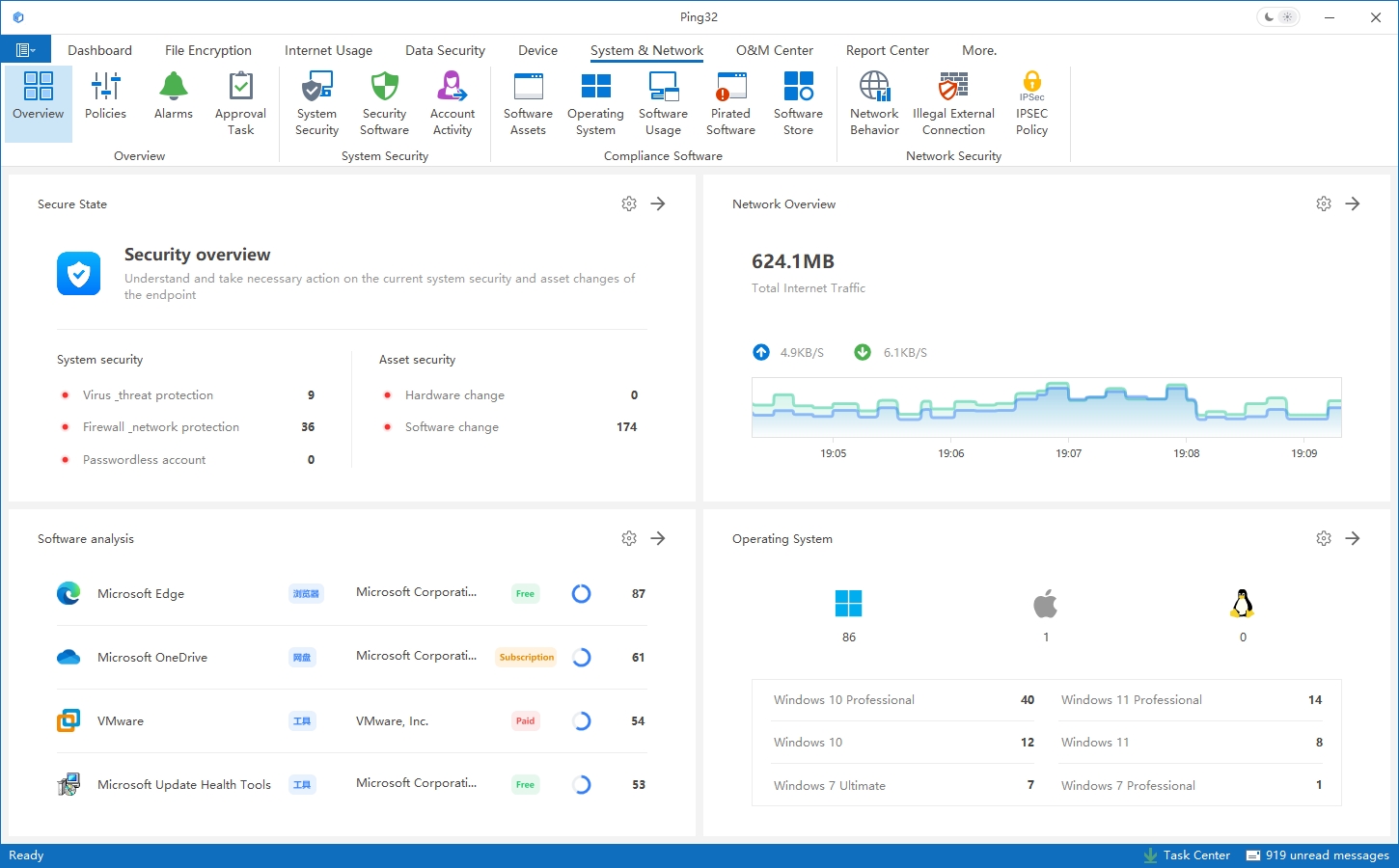
With a modular architecture, organizations can deploy Ping32 incrementally based on business needs, and scale quickly as requirements expand. A clean management interface and global support make it suitable for multi-site and cross-region environments—enabling unified policy enforcement and centralized control.
3. Ping32 Core Capabilities: End-to-End Protection Across Data and Endpoints
One of Ping32’s key strengths is its end-to-end security coverage. By consolidating enterprise security requirements into one platform—endpoint management, data protection, access control, and behavior auditing—Ping32 reduces operational complexity and lowers the cost of security management.
1) Endpoint Security Management: From Visibility to Proactive Protection
Ping32 provides powerful endpoint security management, enabling real-time monitoring of device status and ensuring all corporate endpoints (desktops, mobile devices, servers, etc.) meet security standards.
-
Collects key endpoint attributes in real time (device status, network address, etc.)
-
Automatically detects security events (unauthorized outbound connections, unapproved software, offline alerts, etc.)
-
Improves IT operations with remote assistance, remote wipe, and asset inventory capabilities
2) Transparent File Encryption: Secure Data at Rest and in Transit
Ping32 continuously innovates in data protection. Through strong file encryption, sensitive enterprise data remains protected throughout storage and transfer—whether on local endpoints, removable media, or across networks.
-
Real-time file encryption: Driver-level encryption protects files from the moment they are created. Even if stolen, attackers cannot interpret the content.
-
Transparent encryption mechanism: Files are automatically encrypted without manual user actions. On trusted corporate endpoints, encrypted files can be used normally and seamlessly, enabling efficient collaboration.
-
Stable, kernel-level encryption support: OS kernel-level encryption helps ensure zero file corruption during encryption/decryption, improving reliability and avoiding file damage risks seen in legacy approaches.
3) DLP and Traceability: Prevent Exfiltration and Track Where Data Goes
Ping32 provides DLP capabilities that monitor and record sensitive data exfiltration in real time, helping organizations identify outbound destinations and evaluate risks quickly.
-
Audit & traceability: Fully records data activity trails for auditing, investigation, and accountability.
-
All-channel protection: Unified control across USB, email, printing, IM, browser uploads, and other outbound channels.
-
Sensitive content identification: Detects high-value information such as design documents, source code, and contract materials.
-
Outbound permissions & approval workflows: Fine-grained policy control combined with flexible approval processes to prevent misuse and mistakes.
4) A Comprehensive Security Capability Framework
Beyond core data protection and endpoint security, Ping32 offers rich extension modules that cover broader enterprise security governance needs:
-
Software compliance & asset governance: Automated software inventory, piracy detection, and remediation improve IT management efficiency while reducing legal and security risks at the source.
-
Device and peripheral control: Detailed access control for USB and removable storage, backed by policy configuration and real-time alerts, prevents data leakage and malware propagation through unauthorized devices.
-
Network behavior & access governance: Deep monitoring and policy control over website access, application traffic, and communication protocols helps regulate user behavior and reduce the risk of visiting malicious sites or leaking sensitive information. Ping32 also provides content inspection and control for common channels such as IM and email.
4. The Core Value Ping32 Delivers
1) Simplified Operations and Better User Experience
A clean, intuitive interface and smart features help users get started quickly and operate efficiently—reducing training and support costs.
2) Comprehensive, End-to-End Protection
Ping32 delivers a full-spectrum security framework—from device monitoring and privilege management to DLP and intelligent risk analysis—ensuring every critical link in the enterprise environment is monitored and protected.
3) Faster Incident Analysis and Response
Ping32’s aggregated search consolidates multiple data sources to deliver accurate, fast results. Whether locating sensitive files or identifying potential endpoint risks, teams can obtain needed information quickly—significantly improving efficiency.
4) Innovation in Databases and Storage for Performance at Scale
Ping32 improves performance and reliability through a modern data architecture that integrates multiple engines such as MySQL, ElasticSearch, Redis, and MinIO. This ensures efficient storage and retrieval, fast responsiveness under large-scale workloads, and high performance for complex query scenarios.
5. Industry Applications: Proven Across Multiple Sectors
Ping32 has been widely adopted across industries including finance, manufacturing, education, healthcare, and public services—delivering measurable improvements in data security, operational efficiency, and compliance.
-
Finance: Protects sensitive assets such as customer data and transaction records. Ping32 provides precise leak traceability and risk grading to keep financial data secure during storage and transmission.
-
Healthcare: Protects patient privacy and medical records through file encryption and leak traceability, ensuring data is not misused or exposed.
-
Education: Provides strong protection for research data and academic materials. With DLP and endpoint management, institutions can prevent leakage of sensitive information and generate audit-ready reporting.
6. Frequently Asked Questions (FAQ)
Q1: How does Ping32 ensure sensitive enterprise data does not leak?
A: Ping32 uses multi-layered security mechanisms, especially through DLP. It provides real-time monitoring and sensitive content identification across multiple outbound channels—such as file uploads, email sending, and instant messaging. With intelligent analytics, Ping32 can accurately detect potential leakage behaviors, trigger alerts for high-risk actions, and prevent unauthorized access or outbound transfer of sensitive data.
Q2: How does Ping32’s encryption protect enterprise data?
A: Ping32 provides strong file encryption from the moment a file is created. Encrypted files can be used seamlessly within trusted corporate endpoints. If a file leaks outside the organization, it typically cannot be opened normally or appears as unreadable content—helping ensure the security of confidential documents.
Conclusion
In today’s increasingly severe cybersecurity landscape, Ping32 is a unified enterprise security platform that helps organizations address threats comprehensively—across endpoints, data, outbound channels, and user behavior. With intelligent data protection, privilege governance, risk evaluation, and multi-layer defense mechanisms, Ping32 enables enterprises to build a solid and sustainable security foundation in complex environments—protecting both digital assets and operational continuity.






 Contact
Contact





































 10 min
10 min 





