As digital transformation continues to accelerate, enterprise business models, management approaches, and operational processes are increasingly dependent on IT infrastructure (IT Assets). From internal management systems and business application platforms to data analytics and decision-support frameworks, stable and controllable IT assets have become the foundation of enterprise operations. As a result, IT assets are no longer merely “technical resources” but strategic resources that directly shape efficiency, security, and competitiveness.
For executives and IT teams, without a clear understanding of the scale, distribution, and condition of IT assets, it is difficult to plan budgets and resources scientifically—and even harder to ensure stability across critical business chains. More realistically, once a key asset suffers a failure, configuration anomaly, or unauthorized change, the impact may range from business delays and productivity loss to system outages and process paralysis. In severe cases, it can even affect external delivery and contractual performance, creating direct financial losses and reputational risk.
From an operational perspective, IT assets are primarily composed of hardware and software: hardware provides computing power, storage capacity, and network connectivity, while software carries business logic, process control, and data-processing capabilities. Core functions such as production management, sales operations, financial accounting, and human resources rely heavily on continuous IT availability. Instability at any critical node can quickly escalate into enterprise-wide risk.
From a data perspective, IT assets are the direct carrier of enterprise data. Customer information, financial data, R&D materials, and other critical information are stored on hardware devices and operated through software systems. Hardware aging, system vulnerabilities, or improper configurations may lead to data loss, leakage, or tampering, resulting in economic impact and compliance risk. As data value rises, enterprises become increasingly dependent on data, and the stability, reliability, and security of IT assets directly determine data integrity, availability, and confidentiality.
In addition, IT assets also enable decision-making and innovation. By continuously accumulating and analyzing business-system data, enterprises can better understand operational performance, identify market trends, and optimize resource allocation—improving both the rigor and responsiveness of decisions. Strong IT asset management is the foundation for business innovation, process optimization, and digital transformation. As security and compliance requirements tighten, enterprises must achieve “asset visibility, status traceability, risk assessment, and policy execution.” Only by clearly defining asset scope, operating status, and risk exposure can organizations effectively implement security policies, reduce operational risk, and ensure stable, continuous business operations.
Components and Classification of Enterprise IT Assets
Enterprise IT assets are typically divided into two major categories: hardware assets and software assets. Each delivers different business value and corresponds to different risk surfaces.
Hardware assets are the physical foundation of IT systems, including servers, employee endpoints, network devices, storage systems, and data-center/server-room infrastructure. Servers host core business applications and data storage; employee endpoints support daily work and access to internal systems; network devices ensure the stability and security of internal networks; storage systems enable centralized data management; and data-center infrastructure (such as racks, power systems, UPS, and cooling) ensures reliable operating conditions. Hardware performance, reliability, and maintenance maturity directly affect business efficiency and continuity—device aging, abnormal operation, or unauthorized changes can introduce significant risk.
Software assets are the tools that directly power business operations, including operating systems, databases, business applications, office software, and development/security tools. Operating systems provide the runtime environment for hardware; databases store and manage core data; business applications support critical workflows; office software enables collaboration and information processing; and development/security tools help keep systems stable and secure. Software version status, license compliance, and usage scope directly influence compliance exposure, operational efficiency, and the attack surface. Without visibility and control over software assets, enterprises are more likely to face licensing violations, audit challenges, and latent security threats.
Therefore, IT asset management is not merely an IT operations task—it is closely tied to strategic planning and risk management. Only by managing hardware and software under a unified framework, continuously tracking configuration, distribution, usage, and changes, and turning monitoring and analysis into actionable decisions can enterprises truly achieve “asset visibility, risk control, and executable policies.”
Real-World Challenges in IT Asset Management
As enterprise digitalization deepens, IT assets typically become large in volume, widely distributed, and frequently changing. Traditional approaches that rely on manual registration or scattered tools increasingly fail to meet management needs. Common challenges include:
- Asset information fragmentation: hardware and software data are scattered across different systems and spreadsheets, without a unified asset inventory, making it difficult to quickly see the full picture.
- Changes are hard to track: configuration adjustments, software install/uninstall actions, and version updates often lack continuous records, making unauthorized changes difficult to detect in time.
- Incomplete security auditing: without unified auditing of USB access, peripheral usage, and file copying, organizations face higher risks of insider leakage and compliance issues.
- Rising licensing and compliance pressure: complex licensing rules, expanding industry standards, and contractual obligations require IT teams to continuously prove “verifiable compliance.”
- High operational cost and error-proneness: manual inventory checks, statistics, and reporting consume significant time and effort; data becomes stale quickly, making a sustained management loop hard to maintain.
- Difficulty in policy execution: overly complex controls or measures that impact business continuity create resistance, resulting in “policies on paper but not in practice.”
These factors mean that even when enterprises recognize the importance of IT asset management, they often struggle to build a complete and sustainable system. Without platform-level support, risks in security, compliance, and operational efficiency accumulate as hidden exposure.
The Value of an IT Asset Inventory and Analytics Platform
The core value of an IT asset inventory and analytics platform is using automation and visualization to transform “asset management” from a one-time inventory exercise into ongoing daily governance. By continuously collecting hardware, software, and endpoint-state data and building a unified asset record, the platform helps enterprises establish a management foundation that is “visible, searchable, traceable, and verifiable.”
For asset visibility, the platform can automatically collect endpoint hardware configurations and software installation/usage information, forming a unified inventory view. This allows management to quickly understand asset quantity, distribution, and state changes, avoiding decision bias caused by delayed information. For risk management, the platform can monitor and prompt on key anomalies—such as changes in hardware health, abnormal changes, or maintenance risks—reducing the likelihood of unexpected failures that disrupt business operations.
For security and compliance, the platform provides an auditable data foundation: enterprises can identify risk points and define controls based on asset and behavior data, and when incidents occur, quickly trace and locate affected endpoints and root causes, shortening response time. Platforms typically also support reporting and historical trend analysis, enabling cost evaluation, refresh planning, and optimization of IT investment. For large or geographically distributed organizations, platforms can consolidate IT data across departments and regions, enabling unified management and centralized coordination, improving transparency, and strengthening the foundation for digital and intelligent operations.
Ping32’s Approach to IT Asset Management
Ping32 takes endpoints as the core and brings hardware, software, and peripherals into a unified collection, monitoring, and control framework. The goal is to provide enterprises with a stable and reliable asset data foundation and extend asset governance into daily management actions that are “executable and verifiable.”
1) Hardware Asset Management
On the hardware side, Ping32 automatically collects key information such as CPU, memory, disk, motherboard, and network adapter details to build a continuously updated asset inventory, enabling real-time visibility into asset scale and distribution. It also continuously monitors hardware configuration changes; when increases/decreases or abnormal configurations occur, alerts can be triggered to help detect unauthorized changes earlier. By combining disk S.M.A.R.T. health indicators, Ping32 can identify potential failure risks in advance, reducing the chances of business interruption or data loss caused by hardware damage. USB ports and peripheral usage can also be included in unified visibility and auditing, minimizing “peripheral blind spots.”
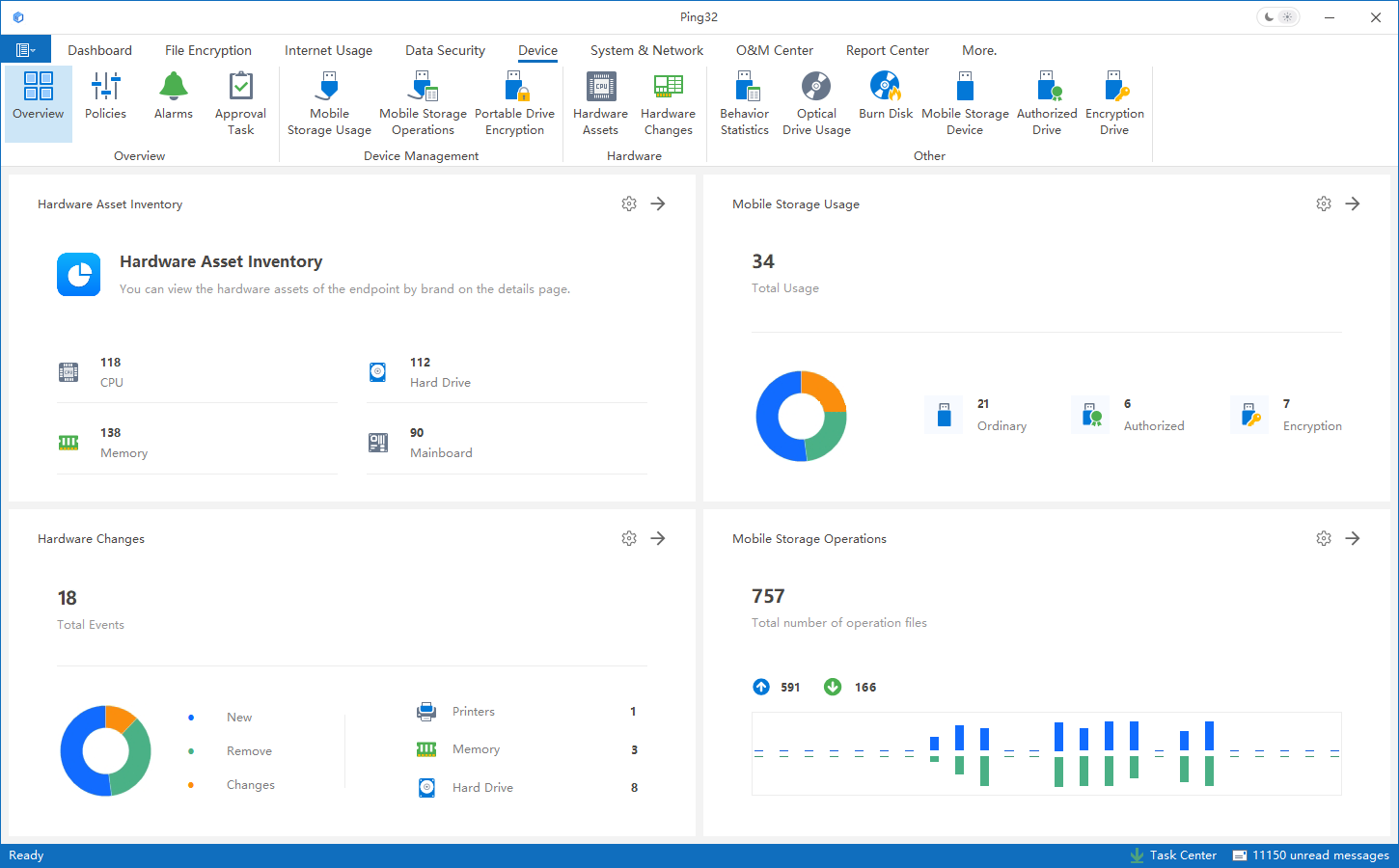
2) Software Asset Management
On the software side, Ping32 can inventory installed and actively used software on endpoints, record installation, uninstallation, and update actions, and provide a unified view of software assets. Organizations can standardize software usage boundaries through allowlists, blocklists, and installation approval workflows, and further reduce licensing and security risks through compliance checks and remote uninstallation. By managing software and hardware together, Ping32 forms a complete IT asset management loop, allowing enterprises to continuously understand asset quantity, location, status, and risk—providing reliable data support for IT operations, security governance, and decision-making.
Practical Case Analysis
Manufacturing enterprise (multi-site, large endpoint fleet): A manufacturing company with multiple factories nationwide operated more than 3,000 endpoints. Manual inventory previously took two weeks and was error-prone. After deploying Ping32, the enterprise completed full asset collection and inventory creation in three days, while enabling real-time monitoring of hardware changes and software installations—significantly reducing operations workload.
Financial institution (strict software compliance): A financial organization needed to audit software installation across the company. Using Ping32’s allowlists, blocklists, and remote uninstallation, unauthorized software could be blocked and removed, elevating software compliance from “spot checks” to a “verifiable” standard while supporting both internal audits and regulatory reviews.
Multinational enterprise (USB/peripheral leakage risk): A multinational organization faced data leakage risks related to USB and peripheral usage. After deploying Ping32, USB connections, burning actions, and file copy operations were fully logged; anomalies triggered alerts, effectively reducing the likelihood of insider leakage and providing auditable compliance records.
Conclusion
IT asset management is shifting from a secondary IT operations task to a core factor that influences enterprise efficiency, security, and competitiveness. With endpoints at the center, Ping32 deeply integrates hardware, software, and peripheral management to help enterprises achieve IT asset control that is “executable, verifiable, and sustainable.” Through visible data collection, behavior auditing, and policy control, enterprises can move from “assets are unclear” to “assets are quantifiable, traceable, and controllable”—building a strong data foundation and governance capability for digital operations, information security, and long-term steady growth.
FAQ
Q1: How does Ping32 collect endpoint hardware information?
A: The system automatically collects key hardware details such as CPU, memory, disk, and network adapter information, and generates a visual asset inventory with continuous updates and change history.
Q2: Can Ping32 monitor USB and peripheral usage?
A: Yes. It supports unified management and auditing for USB/peripheral connections, recording connection time, device information, and key actions, and triggering alerts for abnormal behavior.
Q3: How does Ping32 control software assets?
A: It can restrict software installation and usage through allowlists, blocklists, and installation approval workflows, while recording changes (install/uninstall/update) and supporting compliance checks and remote uninstallation.
Q4: Does Ping32 support remote visibility and centralized management?
A: Yes. It supports remote viewing of endpoint hardware, software, and peripheral status, aggregating everything into a management console for cross-department, cross-region centralized management and analytics.
Q5: Will deploying Ping32 affect daily endpoint usage?
A: Capabilities can be enabled progressively (visibility → audit → control), and policies can be flexibly configured by business scenario to minimize user impact while maintaining business continuity.














 Contact
Contact

































 13 min
13 min 






