In modern enterprise IT environments, endpoint computers are no longer simply personal tools for employees. They have become critical nodes for accessing business systems, processing files, exchanging data, and enabling internal collaboration. As business systems continue to evolve toward digitalization and platform-based architectures, an increasing number of core operations now take place directly at the endpoint.
For small and medium-sized businesses (SMBs), endpoint growth often outpaces the expansion of IT operations teams. Endpoints are distributed across departments, office locations, and increasingly across remote and mobile working scenarios. Under these conditions, relying on manual approaches to handle endpoint issues gradually exposes limitations—lower efficiency, slower response times, and inconsistent management practices.
As a result, endpoint operations are no longer a reactive activity focused on “fixing problems when they occur.” Instead, they are becoming a foundational management discipline that requires long-term planning and sustained investment. Organizations are increasingly evaluating whether a unified endpoint management platform can consolidate dispersed operational tasks, reduce management overhead, and improve overall stability and control.
Risk Factors: Long-Term Hidden Issues Caused by Decentralized Endpoint Management
In environments without centralized endpoint management, organizations commonly face a set of latent operational issues. These may not cause immediate and visible impact, but as the endpoint estate grows, they accumulate into a significant operational burden:
- Distribution of files, software, and system patches relies on manual actions, leading to version inconsistencies
- Remote support methods are not standardized, and resolution quality depends heavily on individual experience
- During device loss, decommissioning, or employee turnover, data handling lacks a unified and consistent process
- Endpoint health is hard to track in time; performance issues are often discovered only after business impact occurs
These are not isolated incidents—they are typical outcomes of decentralized management. Without systematic endpoint management capabilities, organizations often try to compensate by adding more manual effort, with limited results.
Practical Constraints: Why Unified Endpoint Operations Are Difficult to Establish
Even when organizations recognize the importance of endpoint management, implementation often runs into practical constraints related to organizational structure, resource allocation, and tool capabilities:
- Large numbers of endpoints distributed across locations drive up per-device maintenance costs
- Operational tasks depend on individual expertise instead of standardized processes and policies
- Baseline configurations must be repeatedly applied, making long-term consistency difficult
- Remote support efficiency is limited, increasing time-to-resolution
- Identity and login method management becomes complex and costly to maintain
- Lack of structured operational metrics makes it hard to evaluate outcomes and ROI
Under these conditions, endpoint operations often remain focused on addressing immediate issues, rather than forming a stable, sustainable management framework.
The Ping32 Approach: Building Unified and Centralized Endpoint Operations
Ping32 is designed around real-world endpoint operational requirements, integrating dispersed operational activities into a unified endpoint management platform. This helps organizations gradually establish centralized, executable operations without introducing excessive complexity.
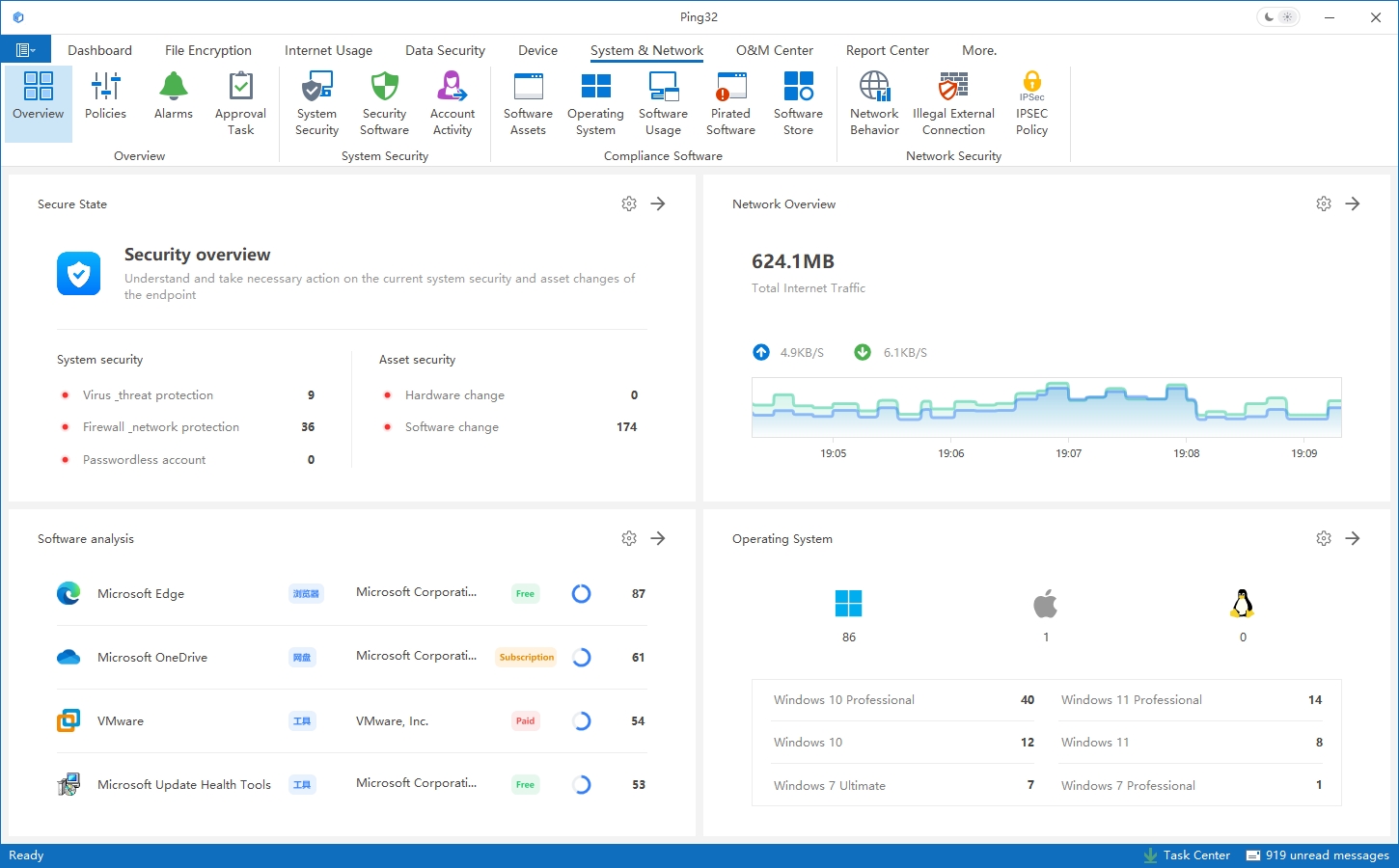
Rather than relying on a single feature, Ping32 is built around key endpoint management scenarios and delivers an integrated capability set covering distribution, support, control, configuration, collaboration, and operational visibility.
File and Software Management: Centralized Distribution to Reduce Inconsistency
Ping32 provides Distribution Tasks to deliver files, software, and system patches to designated paths on endpoint computers, and to support remote software installation and deployment. By centrally configuring distribution tasks, administrators can avoid per-device manual actions, reduce the risk of version drift caused by human error, and maintain a more consistent endpoint environment.
User Support and Issue Resolution: Standardized Remote Assistance
For user support scenarios, Ping32 provides Remote Assistance. Administrators can remotely connect to a user’s desktop to perform actions directly or demonstrate steps, enabling faster responses to system faults or usage issues. Remote assistance supports stable, high-speed file transfer and can record the operation process. Recordings are stored centrally on the local console for later review and internal management, improving support standardization and reducing time lost to repeated communication.
Device Lifecycle Management: Reduce Risk in Exceptional Scenarios
For lifecycle scenarios, Ping32 provides Remote Wipe. In cases such as employee departure, device loss, device decommissioning, or security incidents, administrators can remotely wipe data from the endpoint to reduce management risk. After completion, the system generates a detailed wipe report as an internal record, helping organizations standardize device disposal and incident handling procedures.
Central Policy Configuration: Maintain a Consistent Endpoint Environment
Beyond operational actions, Ping32 supports multiple centralized policy configurations. For energy management, organizations can centrally configure scheduled screen-off, scheduled lock, and scheduled sleep policies, and set up two scheduled shutdown tasks to reduce energy waste. For time management, endpoints can synchronize with server time to prevent system or application issues caused by time inconsistency. For desktop management, administrators can standardize desktop wallpaper and screen saver settings and restrict user changes to maintain a consistent user environment.
Operational Collaboration and Health Visibility: Improve Efficiency and Early Detection
Ping32 provides Ticket Management to centrally collect, track, and handle endpoint-related requests. Administrators can receive endpoint issue information through a unified entry point and respond in a timely manner, improving operational collaboration. The platform also supports statistics and real-time visibility into CPU, memory, and disk utilization. When resource usage exceeds defined thresholds, the system can generate alerts, helping administrators identify potential issues early and reduce impact on business continuity.
In addition, Ping32 supports sending notification messages to all endpoint users or selected users. This can be used for maintenance notices, system changes, and other communications that need unified delivery—reducing communication overhead and improving operational efficiency.
Access and User Management: Flexible Authentication to Reduce Administrative Overhead
At the access and user management layer, Ping32 supports flexible identity authentication options. Organizations can use system-defined users or Windows users for endpoint logins, adapting to different management models and usage scenarios. With unified identity management, organizations can simplify endpoint user administration and reduce the complexity of manual maintenance.
Implementation Path: A Step-by-Step Approach to Centralized Endpoint Operations
In practice, endpoint management is often best implemented progressively:
- Unify distribution capabilities: centrally deliver files, software, and patches
- Standardize remote support: improve response speed and resolution efficiency
- Centralize device control: handle endpoint data quickly in special scenarios
- Unify baseline configurations: reduce repetitive setup and management differences
- Improve collaboration: increase operational efficiency with tickets and notifications
This approach helps organizations establish a stable endpoint operations framework without introducing excessive operational burden.
Endpoint Operations Require Continuous Investment
Endpoint operations are not a short-term project—they are an ongoing management discipline that requires sustained investment and continuous optimization. What matters most is whether endpoint management is executable, consistent, and adaptable as the business evolves.
By consolidating distribution, remote support, device control, baseline configuration, and account management into a single platform, Ping32 helps organizations establish a clear and stable endpoint operations model—shifting IT operations from reactive response to proactive management.
FAQ (Frequently Asked Questions)
-
Will endpoint management affect employees’ daily work?
With reasonable configuration, endpoint management is primarily for operational support and typically does not affect normal daily work. -
What types of content are supported by distribution tasks?
Files, software, and system patches are supported, and remote software installation and deployment are available. -
What scenarios is ticket management suitable for?
It is suitable for endpoint incident reporting, routine IT requests, and centralized management of the issue handling process. -
When is remote wipe applicable?
It is applicable in cases such as employee departure, device loss, device decommissioning, or security incidents. -
Does remote assistance require complex configuration on the user side?
No. Once the endpoint is onboarded via policy, remote assistance can be used without additional user-side configuration.






 Contact
Contact





































 9 min
9 min 





