As enterprise IT continues to mature, data has become one of the most critical production factors in day-to-day operations—especially for small and mid-sized businesses. Design materials, R&D documentation, business files, and customer information are widely distributed across employee endpoints and circulate frequently across roles, systems, and collaboration scenarios. Compared with earlier office models built around internal networks and centralized storage, today’s data movement relies far more on the internet, making the enterprise data boundary both broader and less clearly defined.
With remote and hybrid work becoming the norm, files are no longer exchanged only between internal servers, local endpoints, or internal systems. Instead, they are increasingly transferred through network paths such as browsers, web applications, online collaboration platforms, and business system portals. File exfiltration, once a relatively low-frequency and more controllable action, has evolved into a high-frequency behavior embedded in everyday workflows. Because it often blends seamlessly with normal business operations, traditional methods struggle to distinguish and manage it effectively.
This shift improves operational efficiency while simultaneously amplifying the risk of data leakage. On one hand, employees may—without obvious malicious intent—send files containing sensitive information outside the organization’s control scope via web uploads, online submissions, or attachment transfers. On the other hand, the diversity of network channels and the complexity of technical implementations make it difficult for administrators to quickly determine whether a file was exfiltrated, through which path, and whether the action complies with internal requirements.
For SMBs, these risks are especially pronounced. Compared with large organizations, SMBs often face constraints in security staffing, process maturity, and the depth of tool deployment, making high-cost, heavy-configuration approaches to fine-grained control difficult to sustain. Yet the impact of data leakage does not diminish with company size—incidents can directly damage customer trust, disrupt business continuity, and hinder long-term growth.
At the same time, external expectations are rising. More customers, partners, and industry frameworks are focusing on an organization’s ability to control and explain how data is used and transferred. Companies are increasingly expected to clarify how files are sent outside, whether audit records exist, and whether effective traceability is possible in the event of disputes or risks. In this context, Data Loss Prevention (DLP) is shifting from an “optional capability” to a foundational management requirement that SMBs must seriously evaluate and plan for.
Risk Drivers: How File Exfiltration Risk Forms in Network-Centric Work Environments
In network-centric workplaces, file exfiltration risk does not come from a single behavior or tool. Instead, it results from overlapping changes in work models, technology delivery, and governance requirements. Understanding these drivers is essential for building effective controls.
First, work model changes have reshaped data flow paths. Remote work, cross-region collaboration, and flexible staffing make it common for employees to handle corporate data across different networks, times, and locations. Files are no longer used only within fixed offices and controlled networks; they are frequently transferred and delivered via the internet. This weakens the constraints once provided by physical boundaries.
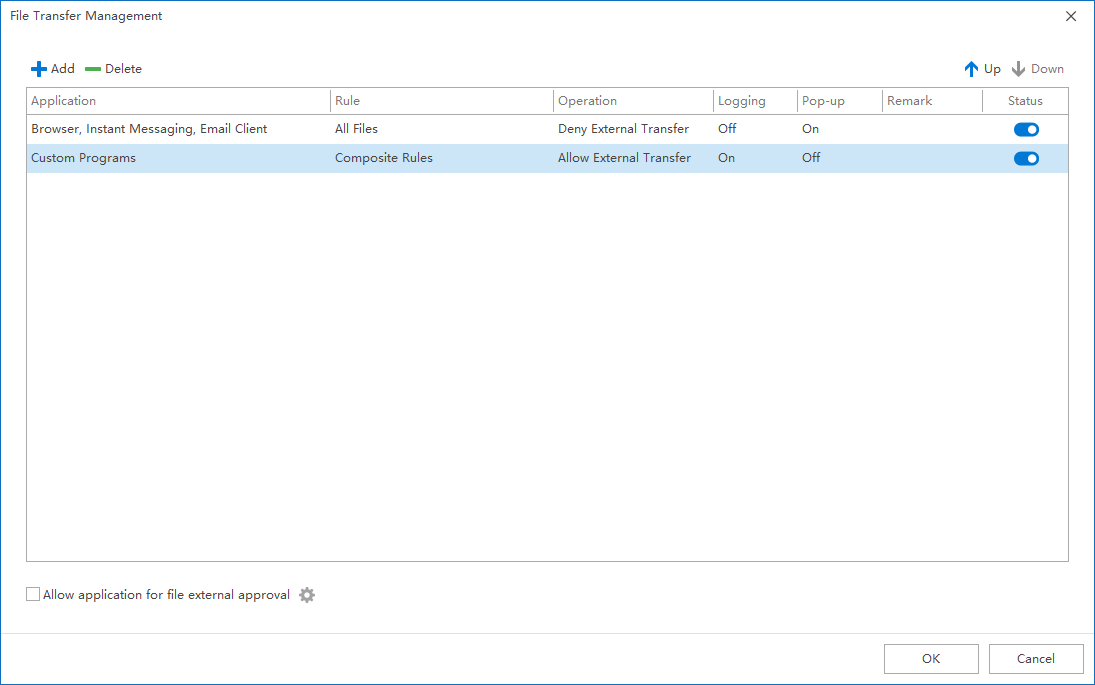
Second, tool and platform diversity increases complexity. Browsers have become a primary work entry point, and many business systems, online platforms, and collaboration tools are delivered through web interfaces. Employees submit materials, share documents, and upload content through webpages. Functionally, these actions are legitimate business steps—but from a data movement perspective, they constitute actual file exfiltration. Without a unified view, these behaviors remain fragmented across tools and systems and are difficult to identify holistically.
Third, rising compliance and customer requirements mean file exfiltration is no longer only an internal management concern. Many partnerships now expect organizations to explain data usage boundaries and movement processes, including whether outbound transfers were authorized, whether traceable records exist, and whether objective evidence can be provided when disputes arise.
In short, the core issue is not “whether exfiltration happens,” but “under what conditions, through which channels, and in what manner it happens.” This also means control cannot rely on simple blocking alone—it requires a more refined, management-oriented approach.
Real-World Challenges: The Gap Between Awareness and Effective Management
Although more organizations recognize the potential risk of network-based file exfiltration, day-to-day management often remains stuck at the awareness stage.
On one hand, exfiltration paths are highly dispersed. Web uploads, online form submissions, and system attachment transfers are spread across different applications and workflows, leaving administrators with partial visibility rather than a full picture. As a result, many organizations struggle to answer a basic question: which files are currently being sent out via network channels?
On the other hand, exfiltration behaviors overlap heavily with normal business operations. For employees, uploading a file is often necessary to complete work. For systems, these actions do not necessarily look like abnormal traffic or unauthorized access. If management tools focus only on network connections or access control, it becomes difficult to distinguish “business-required outbound transfers” from “high-risk outbound transfers.”
Traditional endpoint management approaches also have limited ability to understand content and context. Some tools can identify applications or ports, but cannot combine file attributes, operational context, and exfiltration scenarios into a meaningful decision model. This pushes organizations into a dilemma: overly broad rules fail to control risk, while overly strict rules harm business continuity.
Sustaining controls over time is another challenge. Complex policy configurations, high maintenance costs, and heavy dependence on manual judgment make long-term effectiveness hard to maintain. As business changes, policies become outdated and are gradually weakened or abandoned.
Ultimately, the issue is not that organizations do not care about security—it is that they lack a management approach that can both make behaviors visible and enable gradual, practical intervention.
The Ping32 Approach: Building Understandable and Executable File Exfiltration Management Over Network Channels
Facing the realities of dispersed exfiltration paths, hidden behaviors, and the difficulty of separating business activity from risk, Ping32 does not aim to “stop all outbound transfers.” Instead, it starts from a more fundamental management question: does the organization truly understand how files are exfiltrated—through which network channels and in what business scenarios?
Ping32 treats file exfiltration as an ongoing business behavior that should be continuously observed and analyzed, rather than a one-off anomaly. The starting point is not policy enforcement, but reconstructing real endpoint-side behavior. By combining endpoint management with DLP capabilities, Ping32 focuses on the file lifecycle on endpoints—creation, use, and the key moment when a file leaves the device through a network channel.
In practice, when users perform file-related actions through a browser or network application—such as web uploads, file submissions, or attachment sending—the system can identify the relationship between file operations and network behavior at the endpoint. Unlike approaches that only record network access, this method centers on the “file itself,” capturing file type, source, operation method, and the specific exfiltration scenario. This provides richer, business-semantic data for analysis and decision-making.
On that foundation, Ping32 prioritizes solving the “invisibility” problem first. Through continuous recording and structuring of network-channel file exfiltration behaviors, administrators can gradually gain a more complete view of which files are being sent out, through which channels, and by which roles. This visibility is generated automatically from the endpoint side, reducing management costs and minimizing human bias.
Only after behavior becomes clear does Ping32 introduce policy controls. Policies are not pre-set, one-size-fits-all restrictions; they are built on observed real-world behaviors, allowing targeted management by scenario, file type, or exfiltration method. This approach helps avoid unnecessary disruption to normal operations and reduces long-term policy maintenance burdens.
Meanwhile, audit trails remain a foundational capability. All key actions related to file exfiltration can be recorded in structured form for later audit, review, or compliance explanation. These records are valuable not only for post-incident traceability, but also for policy tuning and management decision-making—creating a sustainable closed loop rather than a one-time configuration.
Overall, Ping32 does not pursue total blocking of network channels. Instead, it establishes an endpoint-based, understandable, executable, and evolving file exfiltration management approach. With the logic of “visibility first, then judgment, then control,” organizations can steadily improve control over outbound file movement in complex network environments without extreme trade-offs between security and productivity.
Implementation Path: Advancing Network-Channel File Exfiltration Control in Stages
In real environments, outbound file movement is often tightly coupled with business workflows. Attempting comprehensive control through strong policies in a short time can create resistance and operational disruption. Ping32 therefore emphasizes a gradual implementation path, treating file exfiltration management as a continuous evolution rather than a one-time project.
The core principle is to build an understanding foundation first, then introduce control measures step by step. Each phase has different priorities and required depth:
- Phase 1: Establish visibility and audit foundations
Enable continuous logging of network-channel exfiltration behaviors without changing employee habits, to build stable and objective data views.
- Phase 2: Analyze and differentiate critical scenarios
Use audit data to identify high-frequency exfiltration scenarios, common file types, and involved roles, and distinguish business-essential behavior from risk-exposed behavior.
- Phase 3: Introduce targeted policy controls
Implement fine-grained policies around identified risk points—for example, specific file types leaving through specific network channels—ensuring better fit and higher organizational acceptance.
- Phase 4: Continuously evaluate and optimize
Regularly review policy effectiveness through audit trails and adjust scope or methods as business patterns change, keeping controls effective over time.
Typical implementation steps:
-
Build visibility and audit baselines for network-channel file exfiltration
-
Analyze frequent and critical scenarios to identify risks
-
Apply fine-grained controls to priority scenarios
-
Continuously evaluate and adjust based on audit data
Conclusion: A Sustainable Approach to Network-Channel File Exfiltration Management
In network-centric work environments, file exfiltration through network channels has become unavoidable. The key question is no longer whether outbound transfers should be allowed, but whether the organization can understand, manage, and continuously optimize this behavior. Controls without visibility and audit foundations often lead to reactive responses after risks materialize, while overly restrictive approaches can impose long-term friction on operations.
Ping32 emphasizes an endpoint- and file-centric management approach rather than simple network blocking. By building a cycle of “visibility → judgment → control,” organizations can strengthen control over file movement without significantly changing existing work habits—and maintain space for future audit and compliance requirements.
Over the long term, sustainable file exfiltration management should have three characteristics: deployable, adjustable, and verifiable. Deployable means it can operate in real business environments; adjustable means policies can evolve with changing workflows; verifiable means key behaviors have audit trails as objective evidence. A system built around these principles is more likely to remain effective in dynamic network environments and prepare organizations for future compliance and audit expectations.
FAQ (Frequently Asked Questions)
-
Does Ping32 record all network content?
No. Ping32 focuses on key behaviors and necessary metadata related to file exfiltration for audit and control purposes. It does not indiscriminately capture all network content.
-
How is web upload (Web Upload) exfiltration identified?
The system correlates file operations with browser or network application behaviors at the endpoint to identify upload, submission, and attachment-sending scenarios.
-
Will file exfiltration controls impact normal work?
With staged rollout and scenario-based policies, organizations can manage risk based on real workflows and minimize disruption to necessary operations.
-
How long can audit trail data be retained?
Retention periods can be configured based on internal policies or compliance requirements to support auditing and traceability.
-
Is control limited to browser-based exfiltration?
No. Ping32 is endpoint-centric and can cover multiple network channels and application scenarios. The exact scope depends on the deployment configuration.














 Contact
Contact

































 13 min
13 min 






