Over the past decade, enterprise discussions around data security have largely focused on servers, firewalls, and network boundaries. However, with the widespread adoption of cloud computing, SaaS applications, and remote or hybrid work models, organizations have gradually come to realize a critical fact: data no longer resides solely in the data center.
For many small and medium-sized businesses (SMBs), critical data is created, accessed, and modified daily on employee endpoints—laptops, smartphones, tablets, and a wide range of removable storage devices. As a result, endpoints have effectively become the center of enterprise data flows.
At the same time, working models have undergone a structural shift. Hybrid work, geographically distributed collaboration, and outsourcing are now the norm. Employees are no longer confined to fixed desks or internal networks. Data paths have become longer and more fragmented: files may be copied or transferred via USB drives, external hard disks, mobile phone cables, or even debugging interfaces—often outside the visibility of traditional security systems.
For SMBs, the real challenge is not whether data security matters, but how to embed security requirements into daily operations under limited budgets and IT resources. Unlike large enterprises that can deploy layered security architectures, SMBs need a sustainable, endpoint-focused mobile device management approach that works continuously without significantly increasing administrative complexity.
Why Data Leaks from Endpoints and Peripheral Devices
Real-world observations and implementation experience show that endpoint data risks rarely stem from a single factor. Instead, they are usually the cumulative result of long-term changes in working practices. These changes are not inherently wrong—many are necessary to improve efficiency and support business growth. However, when organizations lack adequate policies, technical controls, and audit mechanisms, risks gradually shift from “manageable” to “invisible.”
The most fundamental factor is the evolution of work patterns. As laptops become the primary work device, business activities increasingly occur outside the internal network. The volume of locally stored data grows, and once data is transferred via peripheral interfaces, security measures that rely solely on network boundaries often lose effectiveness.
In addition, USB drives, external hard disks, and other peripherals remain widely used for data transfer. Compared to cloud sharing or system-based workflows, peripherals offer plug-and-play convenience and independence from network connectivity, making them practical for file delivery, test data handling, and on-site support. Precisely because these actions occur outside core systems, data copying often goes undetected without proper logging and control.
Meanwhile, connecting smartphones or tablets to office computers via data cables has become increasingly common—for charging, debugging, or file transfer. In many organizations, these devices are not formally included in device management programs and are therefore implicitly allowed.
Finally, compliance and audit requirements from customers and partners are becoming more stringent. Organizations are increasingly expected to demonstrate—not just promise—who accessed what data, when, through which device, and what actions were taken.
Why Everyone Knows It Matters—but Struggles to Implement It
In most SMBs, management and IT teams are well aware of the risks posed by mobile devices and peripherals. High-profile data breach incidents and growing compliance pressure have made endpoint security a recognized priority. Yet turning awareness into sustained action remains difficult.
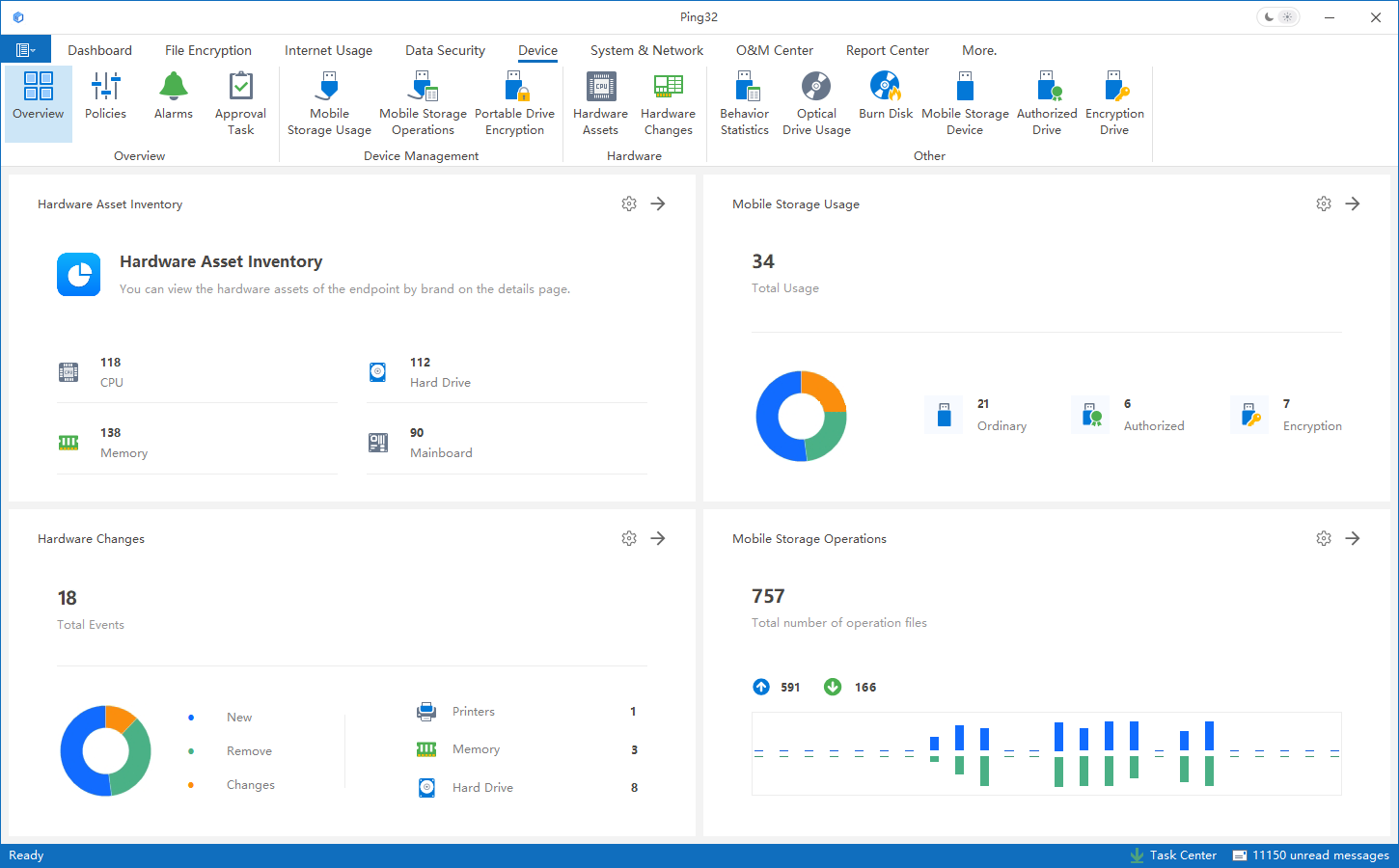
One major challenge is the complexity of endpoint environments. As organizations grow, the number of devices increases, spanning different models, operating systems, and lifecycle stages. Managing assets and usage manually is costly, time-consuming, and prone to gaps.
Another challenge is that USB devices and peripherals remain essential for certain roles. A blanket ban may reduce risk in the short term, but it often disrupts workflows and encourages employees to bypass controls—creating new risks.
At the same time, SMBs typically have limited IT staff. IT teams are expected to handle operations, user support, and security simultaneously, leaving little capacity to maintain complex control systems that require constant tuning.
More critically, the lack of auditable data makes post-incident analysis extremely difficult. When something goes wrong, organizations often cannot reconstruct device connections or data operations, making it hard to assess impact or improve policies.
As a result, many companies experiment briefly with strict controls, only to retreat to lighter-touch approaches based on reminders and recommendations.
Ping32: Comprehensive Control Without Added Complexity
Ping32’s approach to Mobile Device Control is not centered on restriction for its own sake. Instead, it is built around three core principles: visibility, auditability, and configurable policy control.
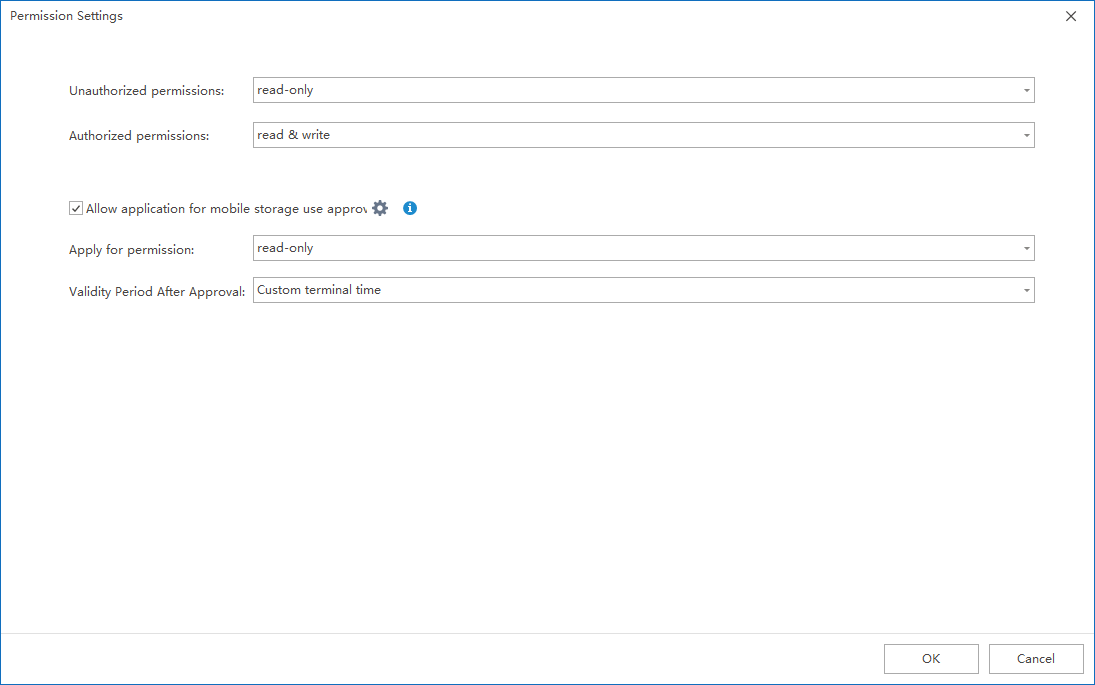
Ping32 treats USB drives, external disks, smartphones, and other peripherals as a unified category of “external devices,” rather than isolated hardware types. Through endpoint-level device identification and logging, organizations gain a clear picture of which devices are connected, how often they are used, and in which business contexts. This visibility provides a factual foundation for policy decisions.
At the policy level, Ping32 enables rule-based control rather than rigid commands. Organizations can apply differentiated controls based on device type, user identity, time windows, or specific behaviors. Roles that genuinely require USB usage can retain necessary access, while critical actions are fully logged.
Most importantly, every control action produces verifiable records. Device connection logs, file operation histories, and policy enforcement data can all be used for internal reviews and audits—turning mobile device management into a routine part of daily operations rather than a purely defensive tool.
A Phased Implementation Path: From Visibility to Control
For SMBs with limited resources, rolling out comprehensive mobile device management all at once is rarely practical. Heavy-handed controls applied too early can disrupt business processes and trigger internal resistance. A gradual approach is more sustainable and effective.
Phase 1: Visibility and Auditing
Enable device identification and logging for USB drives, external storage, and other peripherals. At this stage, the focus is observation rather than restriction.
Phase 2: Risk Identification
Analyze audit data to identify frequently used device types, peak usage periods, and scenarios involving sensitive data. This helps distinguish necessary operations from high-risk behavior.
Phase 3: Policy Pilots
Apply differentiated policies to selected departments or critical roles, adding controls or enhanced logging where appropriate while monitoring business impact.
Phase 4: Continuous Optimization
As the organization evolves, policies are refined and updated to reflect new workflows, roles, and compliance requirements.
This step-by-step approach minimizes operational disruption and increases employee acceptance, making mobile device control a sustainable capability.
Practical and Sustainable Mobile Device Management
Mobile device management is not a one-time security project—it is an ongoing management capability. For SMBs, starting with USB control and gradually expanding to broader peripheral and mobile device management offers a realistic way to improve visibility and control over data flows without significantly increasing administrative burden.
The value of Ping32 lies not in bold promises, but in providing a practical, sustainable path forward.
Frequently Asked Questions (FAQ)
1. Will USB control affect employee productivity?
With well-configured policies, only high-risk actions are restricted. Necessary business usage can remain unaffected.
2. Does implementation require replacing existing devices or operating systems?
In most cases, no. The impact on existing endpoints is minimal.
3. How long can control and audit logs be retained?
Log retention periods can be configured based on internal policies and compliance requirements.
4. Is mobile device management really necessary for SMBs?
When most data is created and handled on endpoints, basic visibility and auditability provide clear operational and compliance value.














 Contact
Contact

































 8 min
8 min 







