As enterprise IT continues to evolve, new instant messaging tools, collaboration platforms, and cloud services keep emerging. Yet email remains deeply embedded in core business workflows over the long term. Whether for external communication, formal document delivery, or cross-organization information exchange, email continues to serve as a stable and standardized channel for data transfer.
From a data-usage perspective, email has two notable characteristics. First, it has broad coverage—nearly every employee uses it. Second, it carries diverse content, including both message text and a wide range of file attachments. As a result, in real-world operations, email naturally becomes one of the primary “exit points” through which enterprise data leaves the internal boundary.
At the same time, sending email is often treated as a routine action rather than a security event. When employees add an attachment, enter recipients, and click Send in a familiar email client, the process typically lacks additional risk prompts or governance constraints. Once a file is successfully sent, the organization’s ability to control that file drops sharply.
In this context, outbound email is shifting from a “communication issue” to a data usage governance issue, becoming a foundational scenario that data loss prevention (DLP) programs cannot avoid.
The inherent uncertainty in outbound email behavior
Unlike system access or permission controls, outbound email risk does not stem from a single technical vulnerability. Instead, it arises from the compounding of multiple uncertainties. These uncertainties mean that even compliant outbound email use can still escalate into a risk incident.
First, email sending is highly frequent and often happens during peak business periods. Under time pressure, employees are more likely to select the wrong attachment or enter the wrong recipient. Second, attachments are highly flexible: the same file format can contain information with completely different sensitivity levels, making it difficult to judge sensitivity based on surface characteristics alone.
In addition, external recipients are diverse—ranging from long-term partners to ad hoc contacts. Without clear authorization boundaries and consistent record-keeping mechanisms, organizations struggle to continuously determine whether outbound sending aligns with internal governance requirements.
In practice, outbound email risks typically concentrate in areas such as:
-
Files sent to external mailboxes without clear authorization
-
The same file repeatedly sent externally beyond a reasonable business scope
-
A lack of unified records, making post-incident verification difficult
These issues are rarely driven by deliberate misconduct; more often, they result from gaps in governance mechanisms.
Limitations of traditional email management approaches
After recognizing outbound email risks, many organizations attempt to manage them through policies or mail-system controls—but these approaches often face clear limitations in execution.
On one hand, policy-based management depends heavily on employee self-discipline, such as requiring registration or approval before outbound sending. In high-frequency business environments, these processes are difficult to sustain and often lack effective technical validation. On the other hand, mail systems typically focus on the communication layer—such as sending/receiving policies or domain restrictions—making it hard to extend controls into local file usage on endpoints.
Common operational challenges include:
-
Mail system logs and endpoint file operations are disconnected, preventing a complete chain of evidence
-
Controls are too coarse-grained, limiting only “whether sending is allowed,” not “what is being sent”
-
Email outbound activity is separated from other outbound channels, resulting in an inconsistent audit view
-
Over-reliance on blocking can disrupt legitimate business communications
-
After incidents occur, evidence collection and analysis can be costly
These limitations often cause outbound email governance to become “tight in the short term, weak in the long term,” making it hard to build stable, repeatable capabilities.
Ping32’s approach to outbound email governance
Ping32 treats outbound email as an endpoint-level data usage behavior, not an isolated communication event. From an endpoint management perspective, it correlates user identity, file objects, and sending actions to build a complete behavioral chain for outbound email.
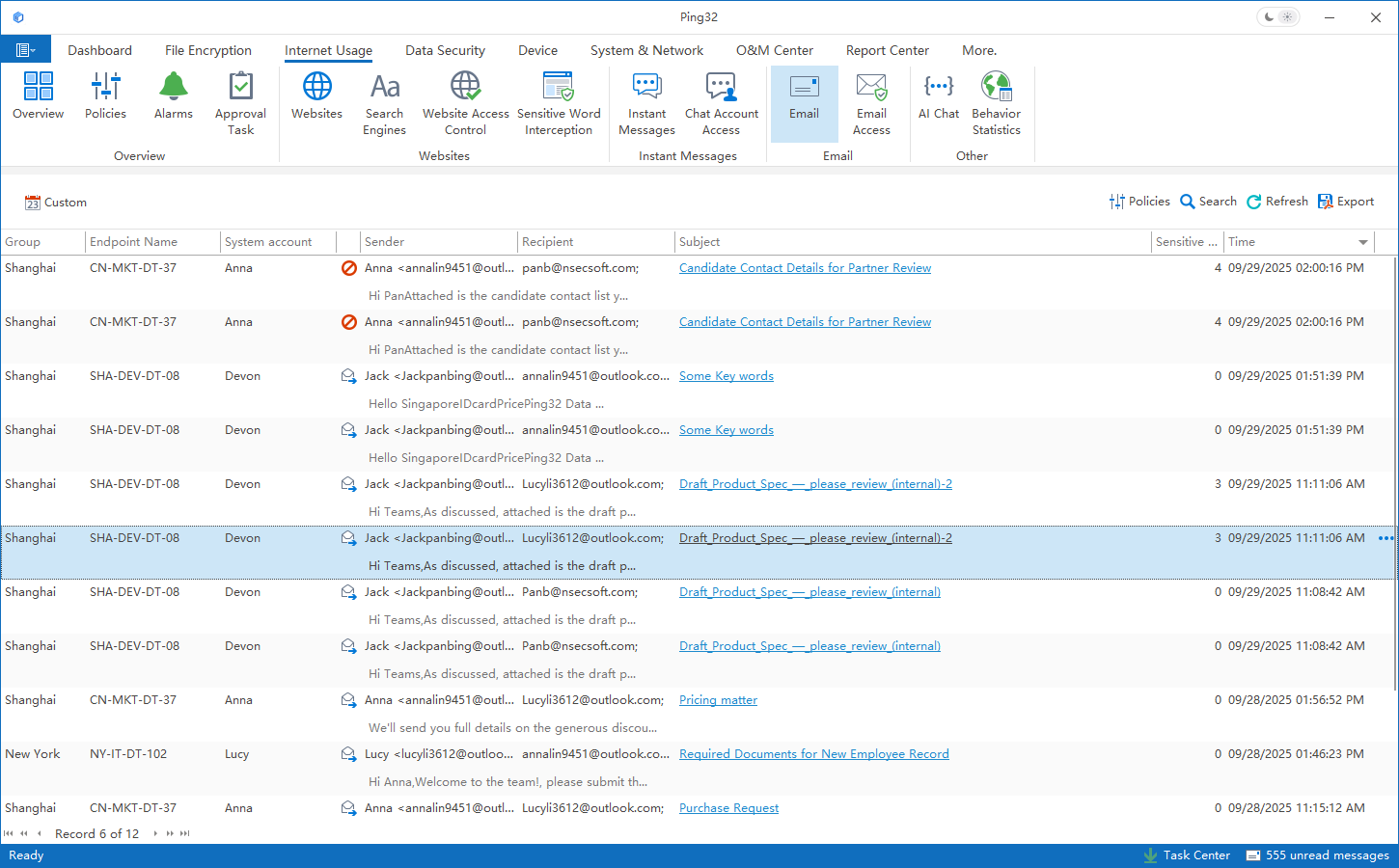
On endpoints, when users send email through an email client—whether using standard mail protocols or HTTPS/SSL-encrypted mail services—the system can monitor and record sending and receiving behavior, covering subject lines, senders, recipients, message bodies, and attachments. For attachment outbound scenarios, the system further records file origin, file attributes, and the outbound action itself, forming searchable audit trails.
With this approach, outbound email is no longer just “whether it was successfully sent,” but a process that can be continuously observed and analyzed. Organizations can clearly understand which files are being sent via email, who performed the action, and how frequently it happens—providing a real, verifiable data foundation.
On top of auditing, Ping32 can integrate with a sensitive content analysis engine to identify sensitive information in email bodies or attachments. When content matches rules, the system can execute policy-based actions such as logging, alerting, or blocking—so governance is based on content and behavioral context rather than a single condition.
Throughout the process, employees continue using their existing email clients with no change in habits or need to learn additional tools, reducing deployment and execution costs.
Balancing governance and efficiency in outbound email
The focus of outbound email control is not simply whether blocking is possible, but whether policies align with real business needs. Ping32 emphasizes differentiated and adjustable policy design, avoiding simplistic handling of complex outbound scenarios.
In practice, not all email attachments require the same level of governance. Routine business materials can prioritize auditing and traceability, while files containing sensitive information or exhibiting abnormal characteristics can be subject to stronger controls. Policies can be flexibly configured based on recipients, senders, file types, file sizes, and other conditions—not only email addresses or domains.
When file outbound controls are enabled, organizations can introduce an approval mechanism for designated files. After an outbound request is submitted from the endpoint, sending is allowed only after approval. The system also supports recording the approver’s review status—such as whether the file was reviewed and when—improving transparency and accountability across the approval workflow.
At the same time, Ping32 can combine leak-tracking capabilities to centrally record and back up files sent externally via email, and to assign risk levels to outbound behavior. The system can identify abnormal operations using time windows and volume thresholds, and apply auditing, alerts, or warnings to files containing sensitive content.
Through these mechanisms, outbound email governance evolves from a simple “allow or block” model into a refined management process built around behavior identification, content analysis, policy control, and risk tracking—so organizations can reduce risk while maintaining day-to-day operational continuity.
A gradual rollout approach for outbound email governance
In practice, Ping32 is best implemented through a phased approach, allowing governance capabilities to integrate naturally into existing workflows:
-
Audit outbound email behavior: capture real sending activity and establish baseline data
-
Identify abnormal or high-risk patterns: based on frequency, file characteristics, and related analysis
-
Introduce targeted policies: enable prompts or approvals for key scenarios
-
Continuously evaluate and optimize: adjust governance boundaries based on audit outcomes
This approach emphasizes incremental strengthening rather than attempting to cover every possible risk in one step.
Making outbound email part of sustainable governance
Email has remained a long-standing office tool because of its stability and universality—but for the same reasons, outbound email governance should not rely on temporary measures. The effective approach is to incorporate outbound email into daily endpoint management and DLP systems, turning it into an operational capability that can run sustainably.
Through endpoint-based auditing and control for outbound email, Ping32 helps organizations gradually establish clear data usage boundaries without changing employee habits. Rather than aiming for one-time coverage of all risks, this approach prioritizes long-term executability and continuous optimization.
FAQ
-
Will outbound email controls change employees’ existing email workflows?
No. Endpoint-based controls can operate without changing how employees use their email clients. -
What does outbound email auditing typically record?
It usually includes sending time, endpoint device, user identity, attachment files, and the corresponding outbound action. -
Can controls be enabled only for certain email attachments?
Yes. Policies can be configured based on file type, attributes, or specific usage scenarios. -
Can outbound records be used for post-incident auditing and accountability?
Yes. Audit trails can reconstruct outbound processes and support subsequent verification and responsibility assignment. -
Are outbound email controls only for external sending?
No. Cross-department or cross-organization email exchanges can also be included in a unified governance view to clarify data flow boundaries.






 Contact
Contact





































 9 min
9 min 





