Pirated and unlicensed software remains one of the most underestimated risks in enterprise IT environments. While many organizations associate piracy primarily with legal exposure, the real impact is far broader. Unauthorized software affects endpoint security, operational stability, audit readiness, and long-term IT governance.
This is why searches for piracy detection software and automated piracy detection are increasingly coming from IT administrators, security teams, and compliance officers rather than legal departments alone. The underlying question is no longer “How do we find pirated software?” but “How do we prevent it from becoming a recurring and unmanaged risk?”
To answer that question, enterprises must move beyond isolated scans and manual audits toward a continuous, policy-driven software compliance model.
Why Pirated Software Persists in Modern Enterprises
In most organizations, pirated software is not the result of deliberate policy violations. It is a structural issue created by scale, decentralization, and operational pressure. As endpoints multiply and software usage becomes increasingly specialized, centralized visibility erodes.
Employees often install tools to meet immediate business needs, especially in engineering, design, data analysis, and research roles. Without a controlled acquisition channel or a clear approval workflow, unlicensed or modified software becomes an easy workaround. Over time, this creates a fragmented environment where IT teams no longer have a reliable understanding of what is running inside the network.
From a governance perspective, this fragmentation has long-term consequences. Once software assets become opaque, compliance enforcement turns reactive. Audits become disruptive. Security incidents become harder to investigate. Most critically, risk accumulates silently until it manifests as a legal dispute, malware outbreak, or operational failure.
The Limits of Traditional Piracy Detection Approaches
Conventional piracy detection typically relies on periodic audits or inventory snapshots. These approaches can identify problems at a specific moment in time, but they fail to address persistence. By the time a report is generated, the environment has already changed.
Manual audits also struggle with accuracy and accountability. Without automation, IT teams must reconcile incomplete asset lists, outdated records, and inconsistent user feedback. Even when pirated software is identified, remediation often depends on manual coordination, which slows response and increases the likelihood of recurrence.
In practice, traditional methods answer only one question: “Is piracy present right now?”
They do not answer the more important question: “How do we ensure that piracy does not reappear tomorrow?”
What Enterprise-Grade Automated Piracy Detection Really Means
Automated piracy detection is not simply about running scans more frequently. In an enterprise context, automation must support continuity, traceability, and enforceability.
An effective piracy detection system should operate as part of the broader endpoint governance framework, continuously correlating software assets with compliance rules and security policies. Detection must be ongoing, not event-based, and results must be actionable rather than informational.
At a minimum, enterprise-grade automated piracy detection should deliver:
-
Continuous identification of installed software across all managed endpoints
-
Context-aware analysis that considers version integrity and abnormal characteristics
-
Policy-driven response options rather than manual remediation
-
Audit-ready records that support internal reviews and external compliance checks
Without these elements, automation becomes superficial and does not materially reduce risk.
Security Implications Beyond Licensing
Pirated software is rarely an isolated licensing issue. From a security standpoint, it represents an uncontrolled supply chain entering the enterprise environment. Cracked installers, unofficial patches, and modified binaries frequently bypass standard integrity checks and security controls.
Once introduced, such software may operate with elevated privileges, disable endpoint protections, or establish unauthorized network communications. In many documented incidents, pirated applications have served as the initial foothold for malware propagation or data exfiltration.
This is why mature organizations increasingly treat piracy detection as part of their endpoint security baseline rather than as a standalone compliance task.
A Governance-Oriented Approach to Piracy Detection with Ping32
Ping32 approaches piracy detection as a component of software compliance governance rather than a single-purpose tool. The focus is on creating a closed loop that connects visibility, detection, enforcement, and prevention.
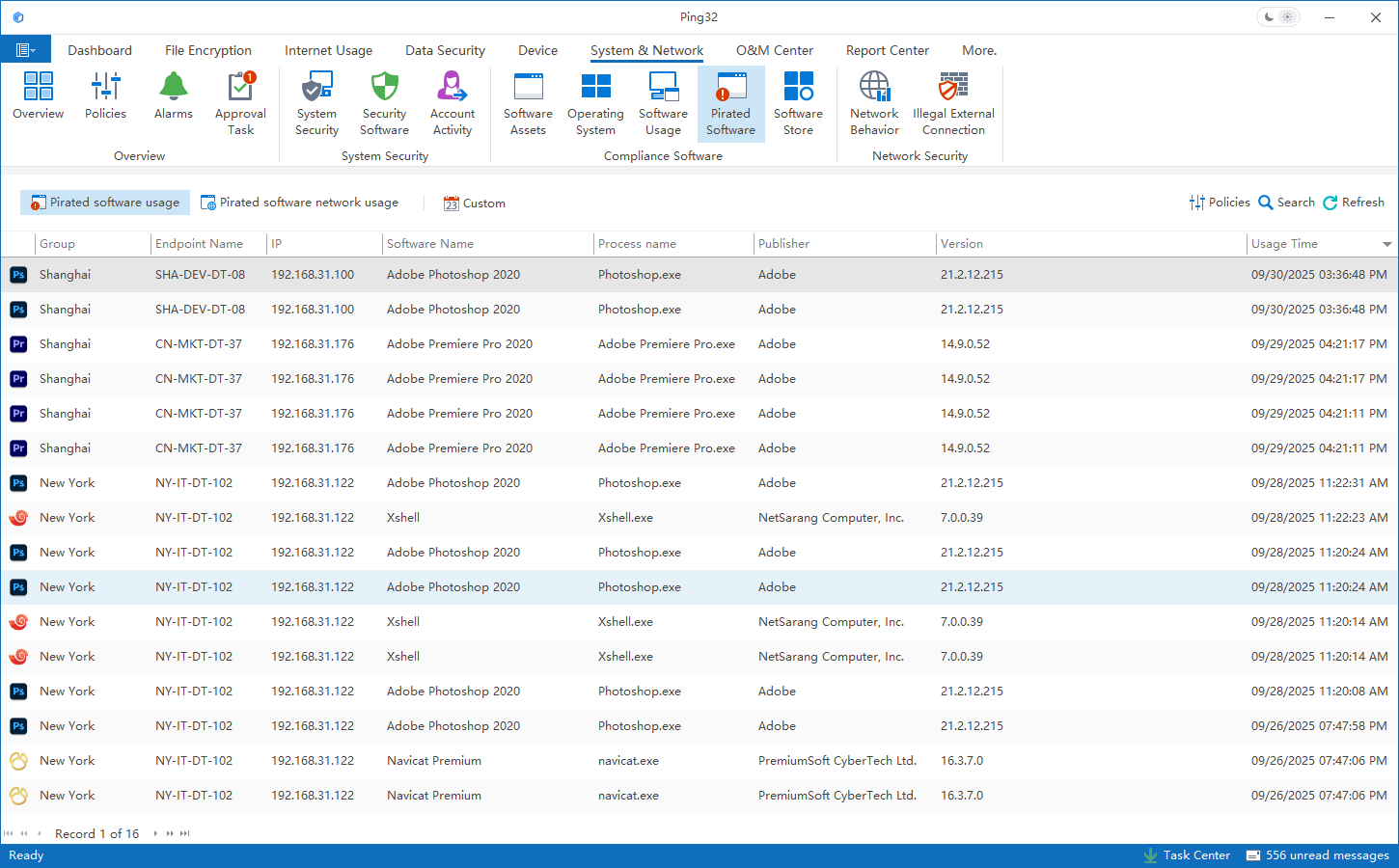
The foundation of this approach is continuous software asset visibility. By maintaining an up-to-date view of installed applications, versions, and usage across endpoints, organizations establish a factual baseline for governance. This baseline is critical, as compliance decisions are only as reliable as the data behind them.
Building on this visibility, Ping32 enables automated identification of unauthorized or abnormal software. Detection results are contextualized within policy frameworks, allowing IT teams to differentiate between critical violations and lower-risk deviations. This distinction is essential to avoid unnecessary disruption while still enforcing standards.
Crucially, detection is directly linked to enforcement. Rather than producing static reports, Ping32 allows organizations to define response actions aligned with risk levels. These actions can range from alerts and notifications to execution blocking or remote remediation. In doing so, compliance moves from documentation to execution.
From Detection to Prevention: Closing the Loop
Detection alone does not eliminate piracy. Sustainable governance requires addressing the conditions that allow unauthorized software to enter the environment in the first place.
Effective prevention strategies typically include controlled installation rights, formal approval workflows, and trusted distribution channels. When users are given a legitimate and efficient way to obtain required software, the incentive to bypass controls decreases significantly.
By combining installation controls, approval mechanisms, and centralized software distribution, organizations can reduce both compliance risk and operational friction. Over time, this shifts the culture from reactive enforcement to proactive governance.
A Practical Enterprise Framework for Software Compliance
Organizations implementing automated piracy detection often follow a phased approach:
-
Establish a comprehensive software asset baseline across all endpoints
-
Define compliance policies based on business roles and risk tolerance
-
Enable continuous detection and automated response mechanisms
-
Introduce preventive controls to regulate future software installation
-
Maintain audit trails to support governance and accountability
This framework emphasizes continuity over one-time cleanup. The objective is not to eliminate piracy once, but to ensure that it remains consistently controlled.
Evaluating Piracy Detection Software for Enterprise Use
When selecting a piracy detection solution, organizations should assess not only detection accuracy but also governance capabilities. Key considerations include:
-
Whether software assets are continuously and automatically identified
-
Whether detection results can trigger enforceable actions
-
Whether installation and execution controls are integrated
-
Whether the system produces audit-ready compliance records
-
Whether policies can be tailored by role, department, or risk level
Solutions that address only one or two of these areas rarely scale in complex environments.
Conclusion: From Reactive Audits to Operational Governance
Piracy detection is no longer a niche compliance activity. In modern enterprises, it is a critical component of endpoint governance and security posture.
Automated piracy detection enables organizations to move away from disruptive audits and toward continuous control. When combined with software compliance management, it transforms piracy from a recurring issue into a managed risk.
The most effective enterprises are those that treat software not merely as an asset to be tracked, but as an environment to be governed—consistently, transparently, and sustainably.














 Contact
Contact

































 8 min
8 min 






