Customer Story | Ping32 Helps an Automotive Company Build a Global-Ready Information Security Foundation
 9 min
9 min As intelligence and digitalization converge across the automotive industry, vehicles are no longer defined purely by mechanical structures and powertrains. They have become cloud-connected, data-driven mobile terminals that deliver software-enabled services. With that shift comes an unprecedented rise in information security requirements. From R&D design files to vehicle operation data, from customer information to overseas operations platforms, sensitive data now flows constantly across internal teams and external partners. Once control is lost, the impact goes far beyond financial damage—brand trust, compliance obligations, and credibility in international collaborations are all at stake.
Across Europe and global markets, TISAX (Trusted Information Security Assessment Exchange) is increasingly used as a key benchmark to evaluate whether a partner can protect information to the required standard. More OEMs and Tier-1 suppliers require vendors to present TISAX results before collaboration, using assurance levels to determine whether information protection meets project expectations. When expanding internationally, a connected and intelligent vehicle company recognized that only rigorous validation through an authoritative framework could earn real trust from global partners. The company stated clearly:
“To compete globally and win OEM confidence, we must build an information security system aligned with international standards.”
Against this backdrop, the company selected the Ping32 enterprise endpoint and data security platform and successfully achieved TISAX AL2, enabling participation in multiple international cooperation projects.
This wasn’t just a certificate—it became a core asset for building trust in the global market.
1. Industry Background and Challenges
The company has spent nearly a decade in the intelligent connected vehicle space, with business spanning overseas vehicle networking, charging operations management, and digital marketing across domestic and international markets. In projects with global OEMs and overseas partners, it must continuously handle sensitive information such as customer data, system architecture details, and operational data. Any leakage could create severe risk to the brand, partnerships, and even business continuity.
TISAX was jointly introduced by the German Association of the Automotive Industry (VDA) and the European Network Exchange (ENX). Its assessment model is based on international standards such as ISO/IEC 27001, while incorporating automotive-specific requirements around supply-chain collaboration, sensitive design information, and test data protection. Because results are shared via a unified platform, TISAX has become a practical “entry threshold” for automotive partnerships.
Within TISAX, AL2 represents an “elevated protection level” for organizations handling relatively sensitive data—such as critical vehicle technology materials, customer personal information, or system operations data. AL2 audits go beyond policies and procedures, focusing on:
-
Whether enforceable endpoint and data security controls are actually deployed
-
Whether key risk scenarios are systematically covered
-
Whether auditability and forensic evidence are clear and verifiable
Before pursuing TISAX AL2, the company faced a pivotal challenge:
How to turn written security requirements into day-to-day capabilities that are visible, controllable, and traceable.
That meant building a technology platform capable of unified governance across endpoints, data, configurations, and behavioral trails—so auditors could verify objective, repeatable evidence.
2. Solution: A Unified Endpoint and Data Security System Powered by Ping32
To meet TISAX AL2 requirements, the company deployed Ping32 with key modules including web browsing control, document security control and auditing, screen security, print security, removable storage control, hardware and device management, system security and IT asset management, software management, operations center, and transparent document encryption—forming an integrated “endpoint–behavior–data” security control system.
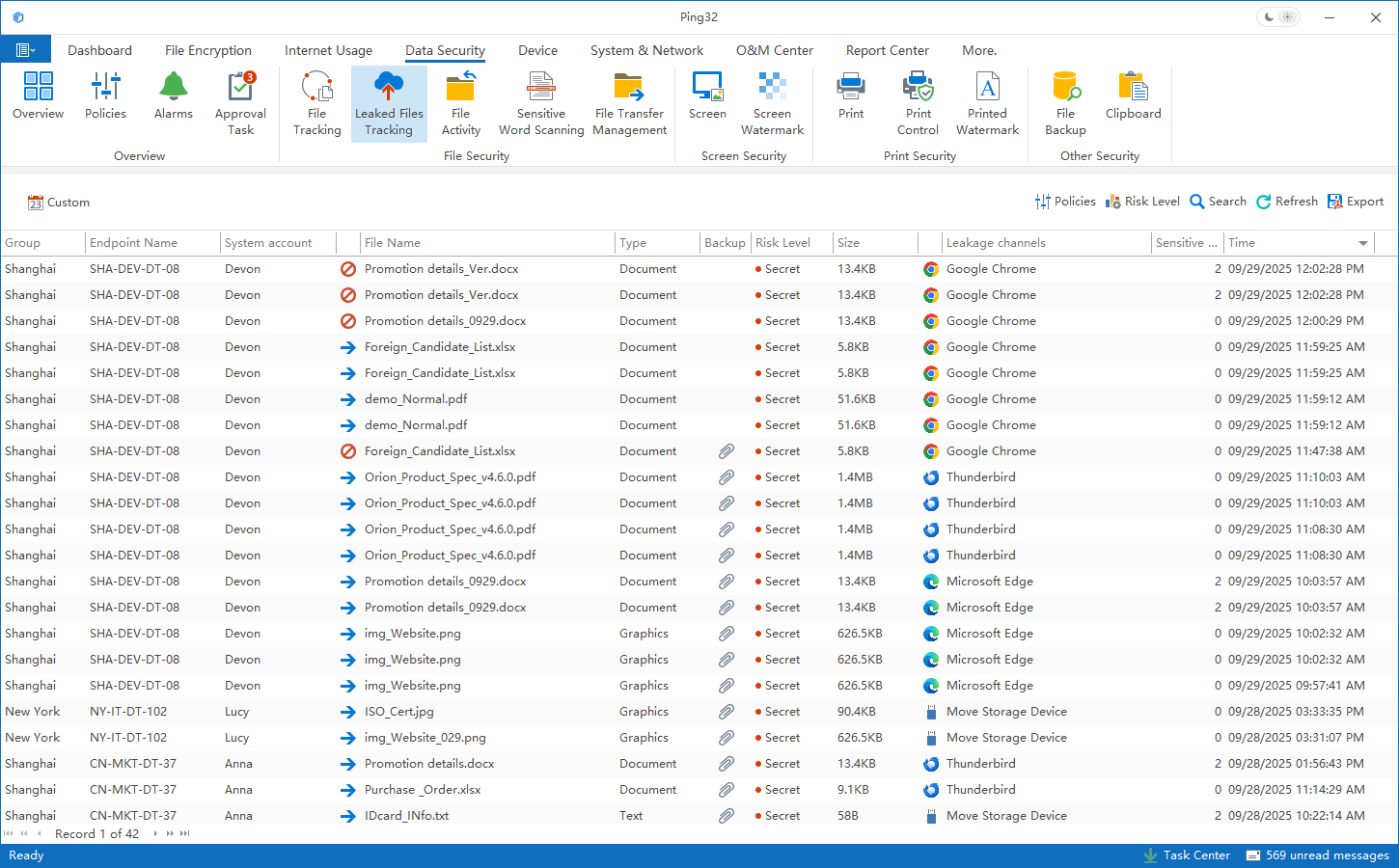
Ping32 first helped classify sensitive data and applied document security controls with transparent encryption to critical directories (project materials, design files, customer documents). Files are automatically protected from the moment they are created. Employees can still edit and use documents locally without extra friction. However, if a document is sent externally via personal email, instant messaging, or public cloud drives, the system automatically detects risk based on policy and enforces blocking, approval workflows, or mandatory encryption. In addition, sensitive content recognition automatically flags files containing key technical terms or structured sensitive data and applies enhanced auditing—ensuring every outbound action is traceable with complete records.
High-Risk Scenario: Removable Storage
Ping32 adopted a “default disable + exception by authorization” approach to centrally manage USB storage devices. Unauthorized devices cannot be used on endpoints. Authorized devices must read/write within encrypted areas, so even if removed from the corporate environment, data cannot be accessed illegally. All plug-in, copy, delete, and related actions are logged—turning “policy” into automatically enforced controls.
Identity and Password Security
The company standardized endpoint password policies: length and complexity requirements, forced rotation within 90 days, prevention of reused and weak passwords, and automatic account lockout after repeated failures. These controls moved requirements from paper to verifiable technical enforcement. For physical security and operational protection, Ping32 enabled a 1-minute inactivity auto-lock policy and prevented users from bypassing or disabling it, reducing risk from shoulder-surfing and unattended devices.
Software Governance
Ping32 enabled a whitelist-based software control model. Only evaluated and approved applications can be installed and run; unauthorized software is blocked automatically, and high-risk tools can be forcibly removed. The platform maintains a complete software asset inventory—including versions, installation time, and owners—supporting both audits and operations. This reduces the risk of malicious tools entering the enterprise network and makes software governance more transparent and standardized.
To mitigate data exposure from lost devices or hardware incidents, the company enabled centralized disk encryption. Encryption keys are managed by the enterprise, and users cannot disable or bypass encryption. Even if devices are lost, sensitive local data remains protected. With comprehensive logging and auditing, Ping32 records critical security actions end-to-end—document access and exfiltration attempts, USB usage, policy changes, login status, and more—allowing security teams to quickly trace incidents and build an end-to-end evidence chain. This proved critical during the on-site TISAX assessment, demonstrating that controls not only “exist,” but are “actively operating.”
Logs and Forensic Auditing
Ping32 centrally records and stores key behaviors—document access and sharing, USB usage, policy changes, logins, and screen locks. With aggregated search, administrators can trace events by user, endpoint, time, or event type to generate clear evidence chains, ensuring “explainable and verifiable” results for both certification audits and daily inspections.
Overall, Ping32 enabled the company to visualize and control critical security points while building a sustainable, verifiable security operating system—providing stable, reliable technical support for passing TISAX.
3. Outcomes and Business Value
During the TISAX AL2 on-site assessment, auditors focused on:
-
● Whether real technical protections are in place
-
● Whether key risks are covered
-
● Whether audit records are authentic and traceable
Ping32’s unified control platform and audit reporting earned strong recognition. The company successfully passed certification and demonstrated mature, systematic information security governance to partners.
This certification significantly strengthened the company’s credibility within the international automotive supply chain, supporting deeper overseas expansion and broader global cooperation. More importantly, the initiative enabled a shift from “passive compliance” to “proactive protection and long-term operations,” laying a solid foundation for future high-end market entry and international collaboration.
4. Ping32 Delivers “Audit-Ready Security Capabilities” for Intelligent Automotive Enterprises
This project shows that TISAX is not merely an external requirement—it can be a catalyst for internal governance upgrades and the true internalization of security capabilities. Ping32 played a pivotal role by providing not only tools, but a clear methodology: making policies enforceable, making risks measurable, and making management auditable.
As more Chinese automotive companies accelerate global expansion, balancing innovation speed with security resilience will be a defining factor in long-term brand success. Ping32 will continue to partner with automotive and manufacturing enterprises to help them earn respect not only through products and technology, but through professional, secure, and trustworthy information protection.
With unified platform capabilities, Ping32 continuously helps customers balance compliance, security, and business growth—safeguarding globalization with confidence.






 Contact
Contact