As digital transformation accelerates, enterprise information systems are increasingly dependent on network platforms and software tools. However, the unauthorized installation of software by employees has emerged as a growing cybersecurity threat. Such behavior not only risks system compatibility issues but also exposes organizations to serious security threats, including data breaches, trojan infections, and ransomware attacks. Therefore, enterprises must implement effective strategies to address this issue and ensure the security of information assets and the continuity of business operations.
Security Risks of Unauthorized Software Installation
- Malware Proliferation
Employees may unintentionally download and install free software embedded with viruses or trojans, which can then propagate throughout the corporate network.
- Data Leaks
Some third-party software may silently collect sensitive information—such as customer data, internal documents, or credentials—and transmit it to unknown servers.
- Resource Consumption and System Degradation
Unverified software may conflict with existing systems, leading to slowdowns, crashes, or other malfunctions that disrupt productivity.
- Compliance Risks
Using unauthorized or pirated software may violate intellectual property laws and lead to legal liabilities, thereby damaging the organization’s reputation.
Common Scenarios of Employee Software Installation
Installing productivity tools (e.g., screenshot utilities, PDF editors, messaging apps) for convenience.
Testing software or scripts using unrestricted system privileges.
Running programs from personal USB storage devices.
Being tricked into installing backdoor programs through phishing or disguised applications.
How to Effectively Control Unauthorized Software Installation
Use of Professional Endpoint Management Tools — Ping32 Unified Endpoint Management
Step 1: Access the Control Interface
In the Ping32 dashboard, navigate to System & Network, then click the Policy button to enter the policy management interface.
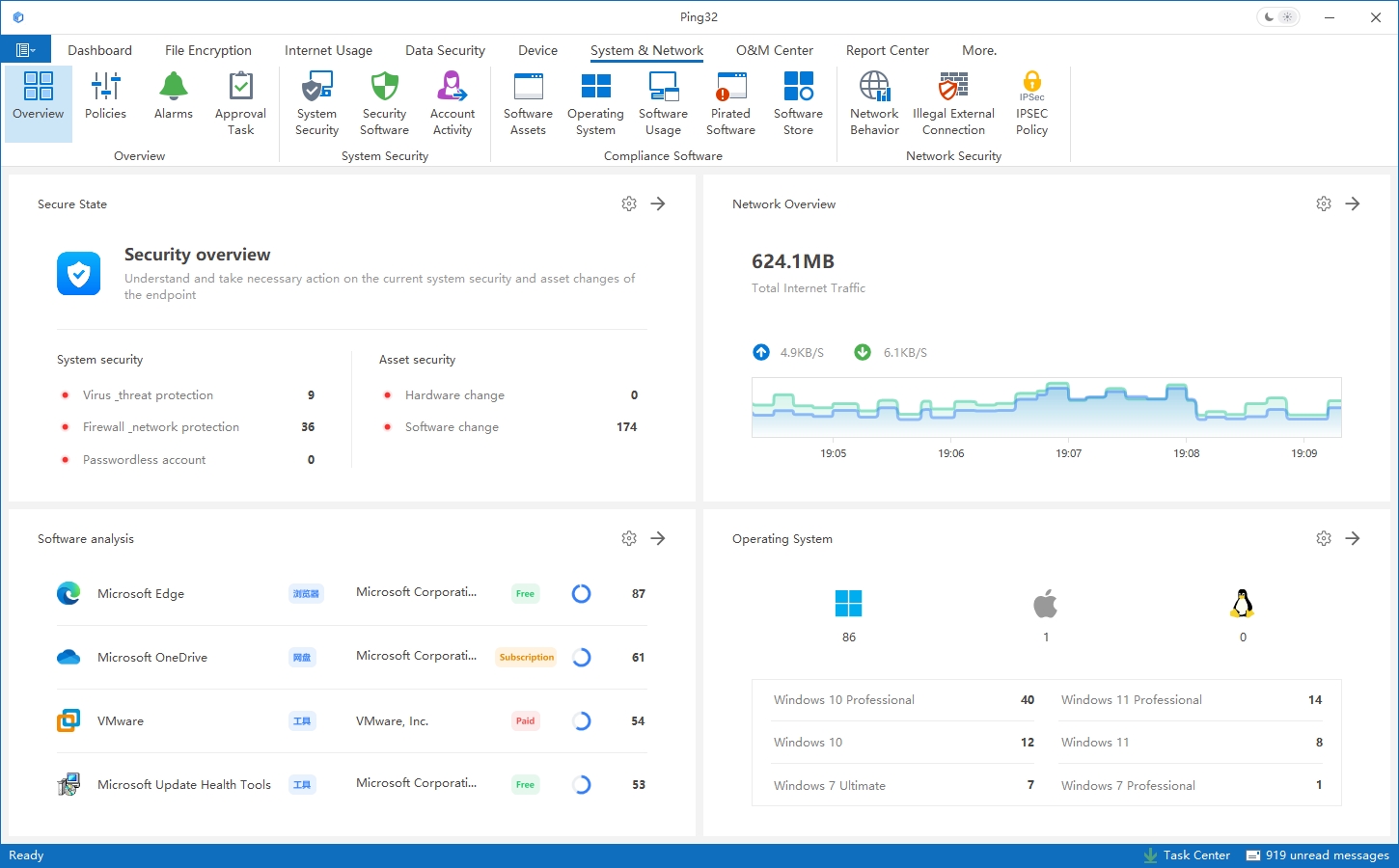
Step 2: Enable Software Installation Policy
Select the desired endpoints using the Select Endpoint button. Enable the Software Installation Control policy. Once activated, all software installations on the selected endpoints will be blocked by default.
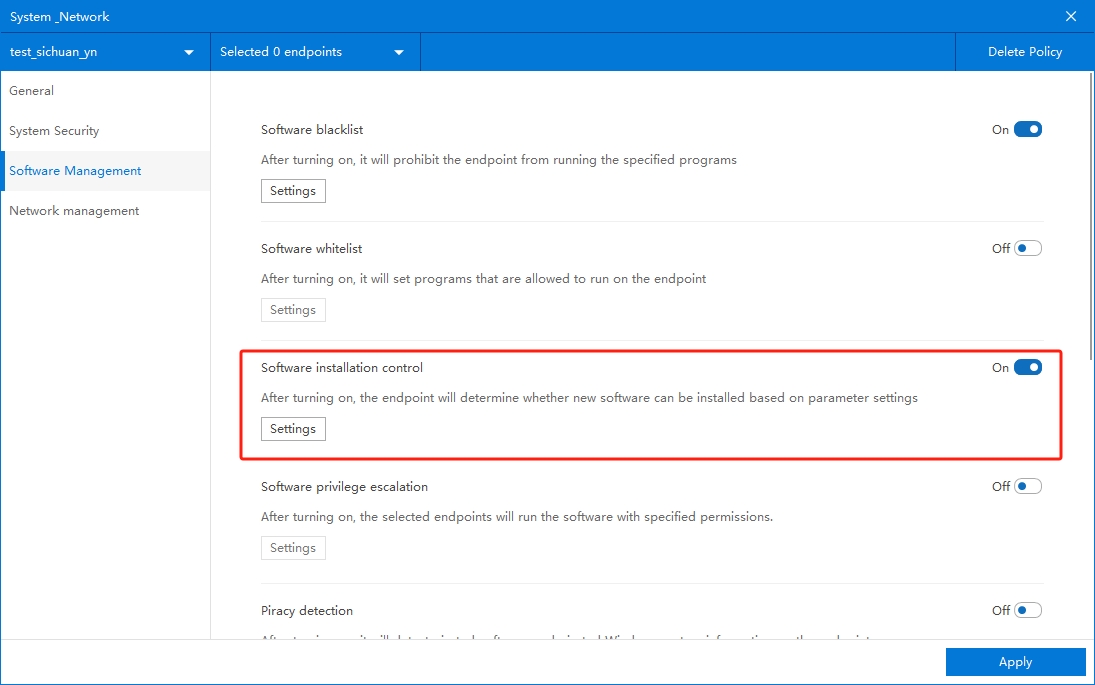
Step 3: Configure Parameters and Whitelist Rules
To accommodate legitimate software installation needs, a software whitelist mechanism is provided.In the Parameter Settings interface, click Add to create new whitelist entries.
Fill in the software description, and use the + button to manually add matching rules. Use the – button to delete them.
You can also import local software directly—rules will be auto-populated.
Click Confirm to save.
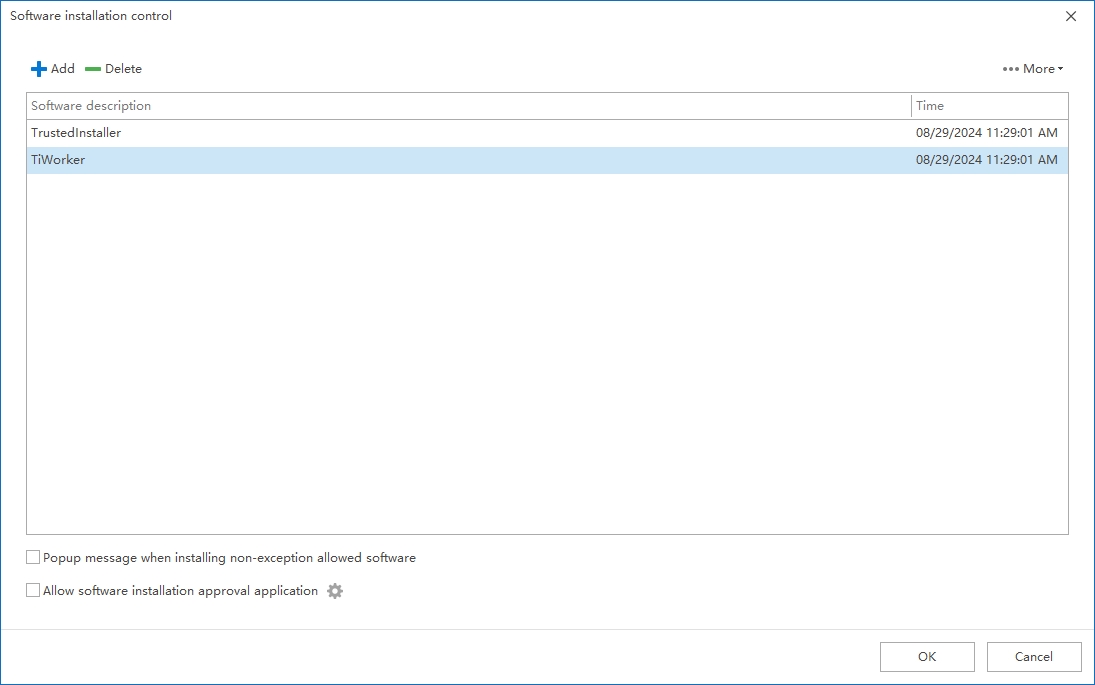
Optionally, select ‘Popup message when installing non-exception allowed software’ to inform users when approved installations occur.
Step 4: Software Installation Request Workflow
To allow employees to request software installation, enable Allow Installation Approval Requests. Approval workflows must be predefined in the Library & Templates section.
Ping32 is a leading endpoint security and management platform in China, designed specifically for internal security control. It provides features such as software installation control, application usage auditing, and peripheral device management.Here are the Core Features of Ping32 Unified Endpoint Management:
- Software Installation Control
Monitors real-time software installations on employee endpoints and automatically blocks unauthorized programs.
- Application Whitelisting/Blacklisting
Allows administrators to enforce standardized software policies by defining permitted or prohibited applications.
- Behavior Auditing and Alerts
Records detailed logs of software usage behavior and provides real-time alerts on abnormal activities.
- Remote Uninstallation
Enables the remote removal of risky applications to reduce potential threats.
- Data Loss Prevention (DLP)
Includes features such as clipboard monitoring, file transfer auditing, and file encryption to prevent data leakage caused by unauthorized software.
With Ping32, enterprises gain full visibility and granular control over endpoint software environments.
On the surface, unauthorized software installation appears to be an issue of access control. However, it more deeply reflects the need for alignment between corporate culture, security policies, and technical enforcement. By adopting a professional endpoint management solution like Ping32, enterprises can shift from reactive to proactive cybersecurity. When combined with policy development and employee education, this solution can significantly reduce the risks posed by unauthorized software—making it particularly well-suited for industries with stringent data security requirements such as finance, healthcare, and government, as well as for mid-to-large enterprises pursuing standardized IT management.














 Contact
Contact

































 5 min
5 min 








