In today’s digital workplace, corporate data no longer resides solely within office boundaries. Sensitive files travel across laptops, mobile devices, and remote endpoints. While this enables productivity and flexibility, it also exposes organizations to serious risks when devices are lost, stolen, or fall out of IT’s direct control.
A critical safeguard for these scenarios is Remote Data Wipe, an essential capability in modern Unified Endpoint Management (UEM) strategies. With Ping32, enterprises can ensure that even when devices leave their control, sensitive data does not.
Common High-Risk Scenarios for Corporate Data
1. Lost or Stolen Devices
When laptops, tablets, or portable drives are misplaced or stolen, the real damage is not the hardware cost—it’s the sensitive information stored within. Without immediate remediation, intellectual property, customer data, or financial records can be exposed.
2. Employee Departure and Non-returned Devices
In some cases, employees leaving the company may fail to return assigned devices. These endpoints may still contain confidential files, project documentation, or customer databases, posing a major risk of data leakage.
3. Device Collection Challenges after Offboarding
Even when devices are collected during offboarding, IT teams cannot always confirm whether sensitive files were copied beforehand. Without strict data wipe protocols, enterprises remain exposed.
4. Remote and Mobile Workforce
Field staff, expatriates, and remote employees often use devices outside corporate networks. If such devices lose connectivity or the employee departs unexpectedly, the company has limited ways to ensure sensitive data is removed in time.
5. BYOD (Bring Your Own Device) Environments
When employees use personal devices for corporate work, the organization has no ownership of the hardware. Ensuring company data is deleted without infringing on personal data and privacy requires precise, policy-driven remote wiping capabilities.
These scenarios highlight a universal challenge: even when devices are outside the company’s control, corporate data must remain protected and compliant.
Ping32 Remote Data Wipe: Last Line of Defense
Ping32 integrates Remote Data Wipe directly into its Unified Endpoint Management platform, enabling IT and security teams to protect sensitive information across diverse scenarios.
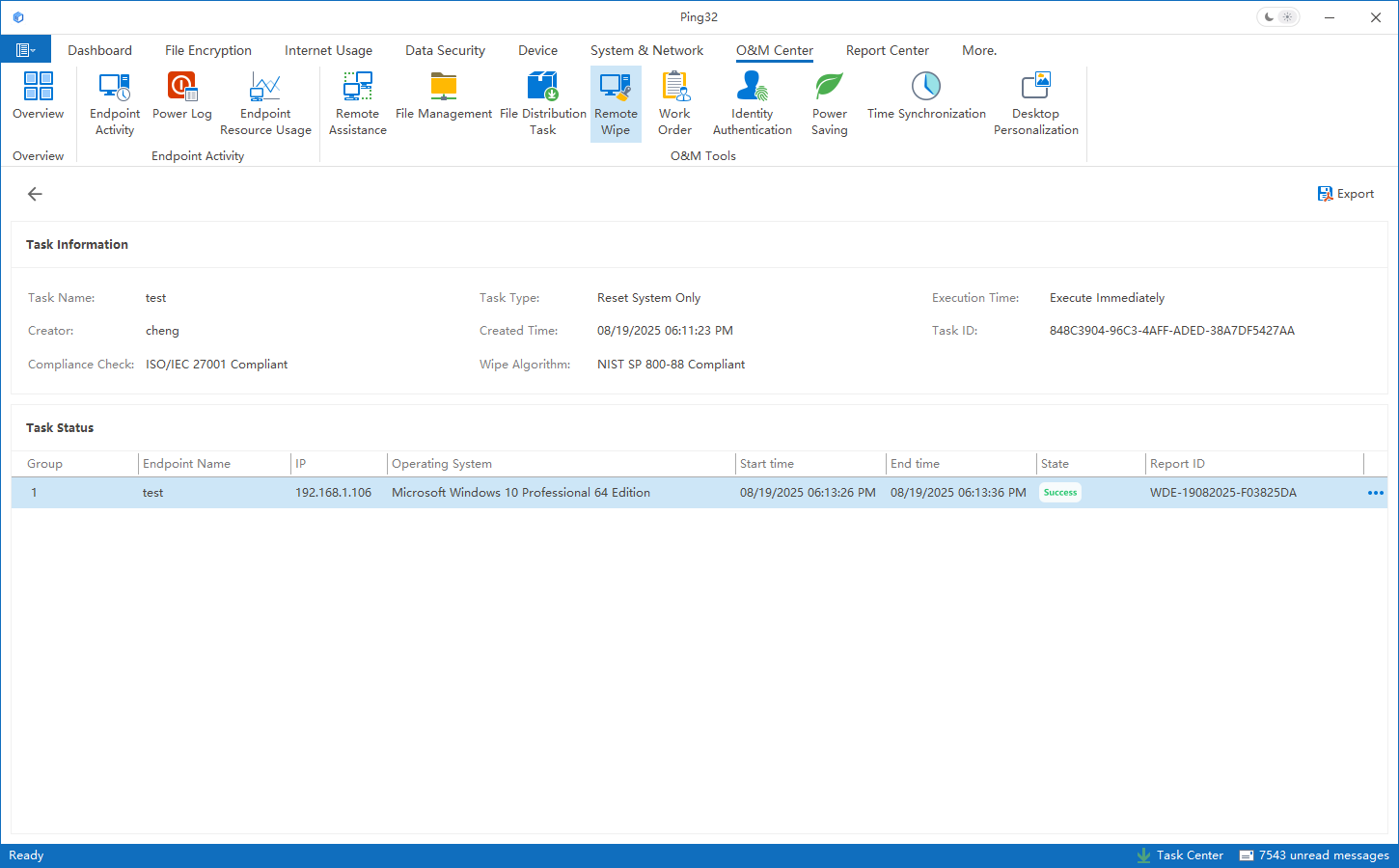
1. Flexible and Granular Control
-
Wipe specific files, folders, or file types without affecting the operating system or personal data.
-
Focus on business-critical assets such as source code, customer lists, or confidential reports.
2. Remote Execution Across Networks
-
Administrators can issue wipe commands from the management console, regardless of the device’s location.
-
Ensures timely response even when devices are outside the corporate environment.
3. Compliance and Audit Readiness
-
Every remote wipe action is logged, detailing who initiated it, when it was executed, and which data was erased.
-
Provides organizations with auditable proof of compliance during internal reviews and regulatory inspections.
4. Integration with Corporate Processes
-
Fits seamlessly into HR and IT workflows: HR initiates offboarding, department managers confirm data scope, IT executes the wipe, and audit teams store the records.
-
Establishes a standardized, traceable, and compliant data removal process.
Why Unified Endpoint Management Matters
Remote Data Wipe is most effective when combined with a comprehensive Unified Endpoint Management (UEM) strategy. UEM ensures that all devices—corporate-owned or employee-owned—are consistently managed, monitored, and secured through a single platform.
By unifying policy enforcement, software distribution, data protection, and remote wipe capabilities, Ping32 enables enterprises to achieve:
-
Consistent device governance across desktops, laptops, and mobile devices.
-
Reduced operational complexity, with IT teams managing all endpoints from a centralized console.
-
Enhanced compliance, with standardized policies for data handling, access, and removal.
Conclusion
Enterprises cannot control every endpoint at all times, but they must always control their data. Lost devices, employee turnover, remote work, and BYOD models all pose significant risks if sensitive information is left unmanaged.
With Ping32 Remote Data Wipe, organizations gain the ability to erase sensitive data quickly, precisely, and compliantly, ensuring information security across every endpoint. Integrated within Ping32’s Unified Endpoint Management solution, Remote Data Wipe is not just a feature—it is the enterprise’s last line of defense.
Ping32: Because devices may be lost, but data security must never be.














 Contact
Contact

































 5 min
5 min 






