back
backAs a cornerstone of the real economy, the manufacturing industry involves a vast amount of sensitive data, including product design drawings, production processes, customer order information, supply chain data, intellectual property, and trade secrets. With the acceleration of digital transformation, enterprise data is becoming increasingly decentralized and networked, significantly increasing the risk of data breaches. Common risks include:

- Insider Misconduct: Employee mistakes or intentional data theft;
- External Attacks: Hacking, supply chain attacks, ransomware threats;
- Third-Party Collaboration Risks: Poor access control for suppliers and partners;
- Endpoint Security: Data leaks from mobile devices and BYOD (Bring Your Own Device) practices.
Traditional security measures (such as firewalls and antivirus software) are insufficient to address the complex scenarios of data leakage. Manufacturing enterprises urgently need to establish a full-lifecycle data security protection system.
Ping32 Data Loss Prevention (DLP) System is a vendor specializing in endpoint security and data loss prevention. Its solutions are widely used in industries such as manufacturing, finance, and government. For the manufacturing sector, Ping32 offers a tailored DLP solution that helps enterprises:Implement data classification and hierarchical management to accurately identify core assets;Enforce dynamic access control based on the principle of least privilege, with behavior auditing;Provide multi-dimensional encryption to protect data throughout its lifecycle;Conduct compliance audits and data traceability to meet regulations such as GDPR.This ensures the security of sensitive data including design drawings, production processes, and customer information.
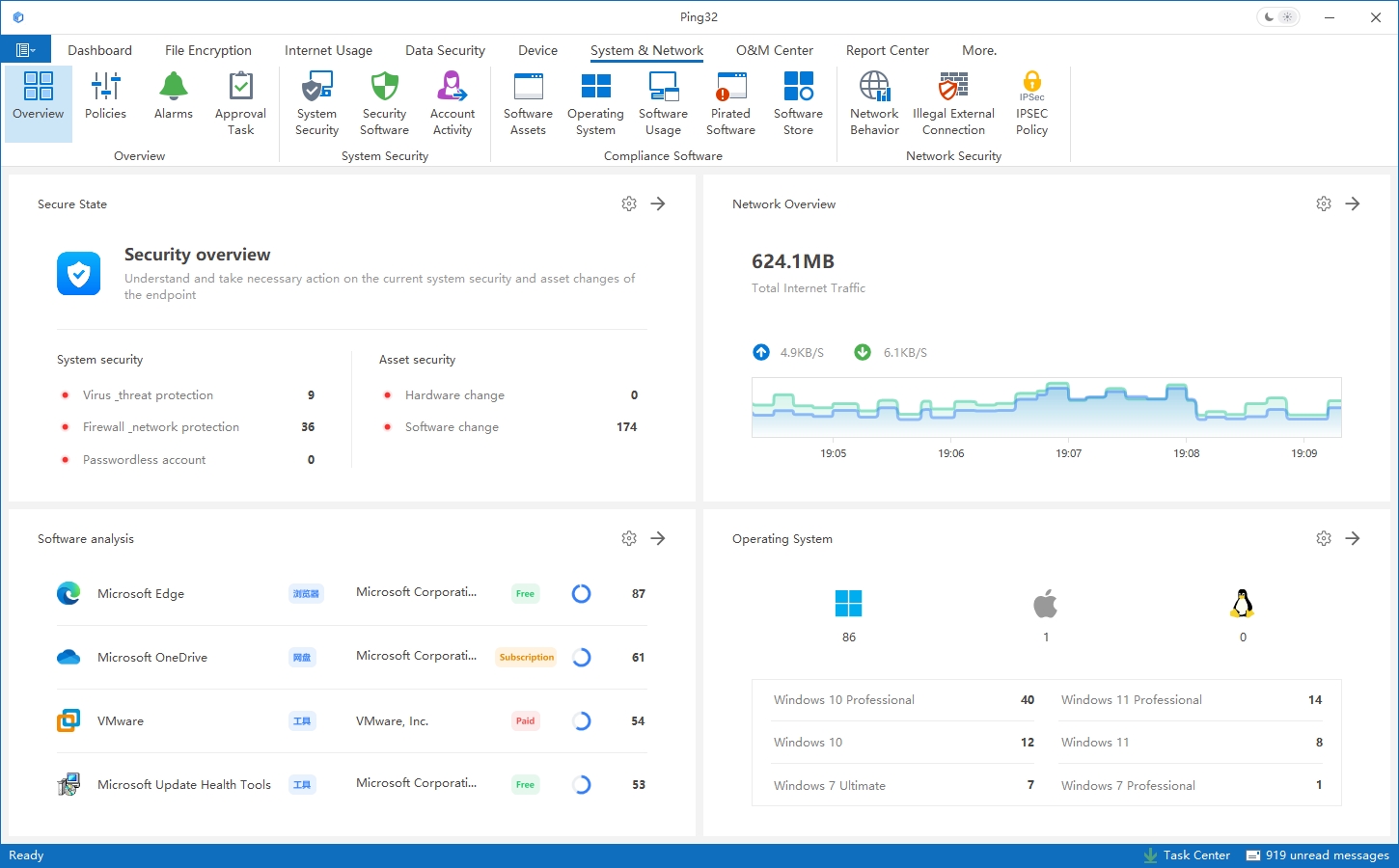
Core Functional Modules
- Transparent Document Encryption
Encrypts design files (e.g., CAD, SolidWorks, PDF) without affecting user habits. Authorized software can still access the files normally. Encryption is automatically triggered during events such as employee resignation, network disconnection, file copying, or uploading.
- Outbound File Control
Files sent externally (via platforms such as email, cloud drives, etc.) require approval. All transmissions are logged and traceable, with support for revocation and watermarking for source tracking.
- Endpoint Operation Auditing
Monitors and logs operations such as USB usage, printing, screenshots, uploads, and cloud drive access. Alerts are triggered for suspicious behaviors such as mass file compression or abnormal data transfers. Supports video playback to aid investigations.
- Device Usage Management
Restricts or disables USB drives, external hard drives, and mobile devices. Supports device whitelisting and encrypted protection for approved USB devices to prevent unauthorized data copying.
- Network Behavior Management
Limits access to specific websites (e.g., cloud storage, email, social platforms), manages IM tool usage , and detects and blocks attempts to leak sensitive files over the network.
- Drawing File Protection
Provides dedicated protection for commonly used design software in the manufacturing sector, such as AutoCAD, CAXA, Pro/E, and SolidWorks. Automatically identifies and encrypts drawing files, preventing leakage through screenshots or other methods.
- Employee Exit Data Control
Automatically analyzes data operations before an employee leaves, archives work data, and creates audit backups to prevent data theft, such as customer lists or proprietary designs.
Solution Advantages
- Zero Trust Architecture: “Never trust, always verify” with least-privilege access by default.
- Seamless Deployment: Transparent encryption ensures business continuity with no user disruption.
- High Compatibility: Supports Windows, Linux, macOS.
- Lightweight Operations: Centralized management platform enables one-click policy deployment, reducing IT costs.
With intelligent recognition, efficient encryption, flexible permission control, and comprehensive auditing, Ping32 establishes a robust defense system for manufacturing enterprises—safeguarding critical information while enhancing overall information security management.
If you require a customized Ping32 deployment plan or feature customization tailored to your manufacturing operations, feel free to contact us. We are here to provide professional consultation and support.






 Contact
Contact





































 4 min
4 min